Notification Channels
How to use Slack, PagerDuty, Opsgenie, MS Teams, Flock, Google Chat, Telegram, Jira, Zenduty, webhooks, and email for getting alert notifications.
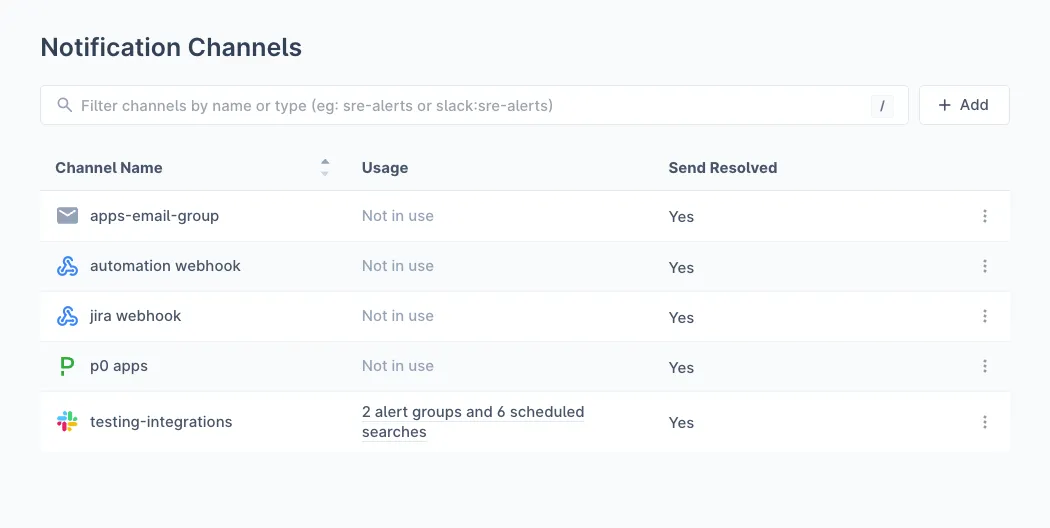
Notification Channels are destinations for Last9 to send alert notifications. We support the following channel types: Slack, PagerDuty, Opsgenie, Webhook, and Email. The Webhook channel supports auto-detection for MS Teams, Flock, Google Chat, Telegram, Jira, and Zenduty.
Adding a Notification Channel
-
Navigate to Notification Channels and click Add
-
Provide the following details:
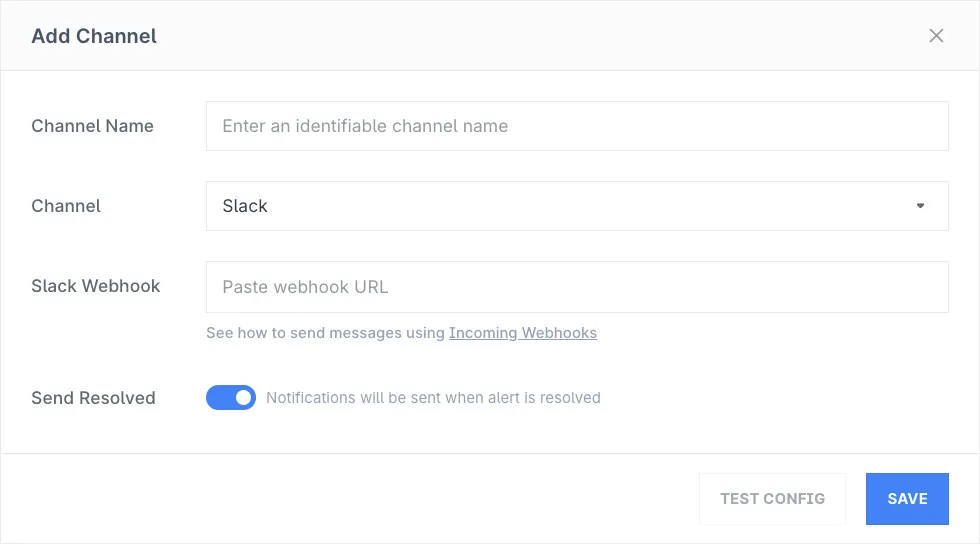
- Channel Name: Descriptive name to easily identify channel destination
- Channel: Choose a channel from the supported integrations list
- Webhook/API Key/Email: Provide the relevant details for the selected channel
- Slack: See how to send messages using Incoming Webhooks. Setup guide
- PagerDuty: See how to use the PagerDuty Events V2 API
- Email: Enter the email IDs to be notified
- Opsgenie: Enter the API key
- Webhook: Enter the webhook URL. Last9 auto-detects and formats for the following platforms:
- MS Teams (
.webhook.office.com) - Setup guide - Flock (
api.flock.com,flock.co) - Setup guide - Google Chat (
chat.googleapis.com) - Setup guide - Telegram (
api.telegram.org) - RequiresTELEGRAM_CHAT_IDheader. Setup guide - Jira (
atlassian.net) - RequiresJIRA_PROJECT_NAME_KEYheader. Setup guide - Zenduty (
events.zenduty.com) - Setup guide
- MS Teams (
- Send Resolved: Enable if you want to be notified when an alert has been resolved, useful for automation of incident management
-
If you’ve selected Slack as the channel, you can also send a test message to the configured channel by clicking on Test Config
-
Click on Save to enable this channel. This channel can now be used in Alert Groups or Scheduled Search to start receiving notification
Usage of a Notification Channel
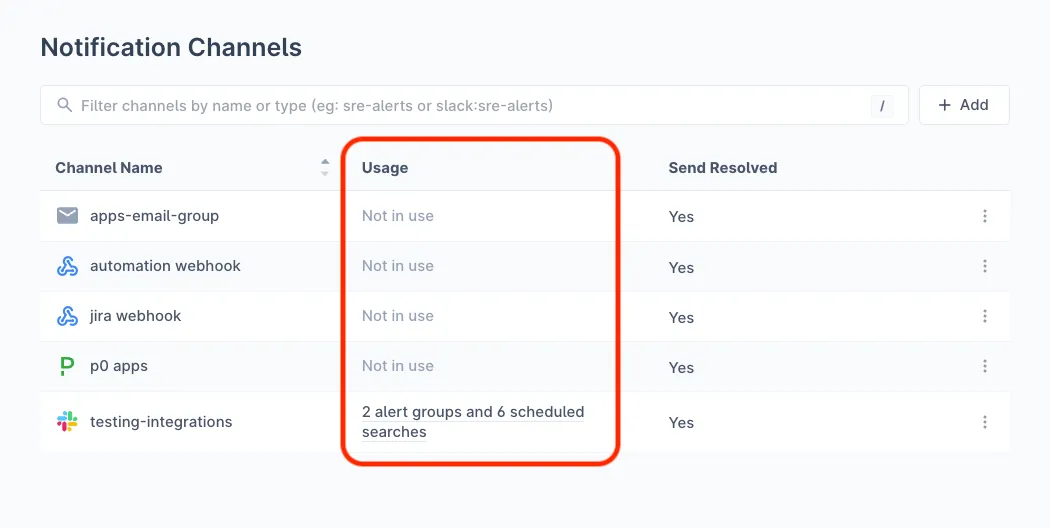
In Notification Channels, you can quickly understand which configured channels are being used and by how many alert groups or scheduled searches.
To view which alert groups or scheduled searches are using a particular channel, click on the relevant channel’s Usage link to view the list. From here, you can also jump to any of the alert groups or scheduled searches.
Notification Payloads
In case you want to further use the generated JSON payloads for custom incident details, automation and workflows, alert enrichment, or integrating with other tools, refer to the following mapping for PagerDuty and Opsgenie.
PagerDuty
| PagerDuty field | Type | Description |
|---|---|---|
| payload | object | |
| payload.summary | string | Title for the incident |
| payload.timestamp | timestamp | The ending time of this alert, in ISO 8601 format |
| payload.severity | string | critical / warning for alerts marked as breach/threat in alert rule |
| payload.source | string | Dedup key for the incident |
| payload.component | string | Empty |
| payload.group | string | Dedup key for the incident |
| payload.class | string | Alert Rule Type |
| payload.custom_details | object | Described below |
| routing_key | string | PagerDuty integration key |
| event_action | string | ’trigger’ for active notifications, ‘resolve’ for resolved notifications |
| dedup_key | string | Dedup key for the incident |
| client | string | ”Last9 Dashboard” |
| client_url | string | Link to health dashboard for the alert in Last9 |
| links | array of objects | Empty array |
| images | array of objects | Empty array |
Custom Details
alert_condition- Condition set on alert. Static alerts, it is of the format.expr > 10based on the threshold configured. For pattern-based alerts, it is of the formatalgo_type(tunable, expr). For example, for a high spike alert set with tunable 3, this would behigh_spike(3, expr)algo_type- Type of alert (static_threshold,increasing_changepointetc)client_url- Link to the health dashboard for this alert on Last9description- Description of the alert. If a description is provided while configuring the rule, it appears here. Otherwise, a default description based on the algorithm, indicator, and entity is shownstart- Starting time of this alert, in ISO 8601 formatend- Ending time of this alert, in ISO 8601 formatexpression- Name of the indicatorentity_name- Entity nameentity_type- Entity typeentity_team- Entity team. IsNoneif not assignedentity_tier- Entity tier. IsNoneif not assignedentity_workspace- Entity workspace. IsNoneif not assignedentity_namespace- Entity namespace. IsNoneif not assignedseverity- Severity of the alert (breach/threat)notification_call- Whether this alert is sent for the first time or repeated (first/repeat)runbook- Link to the runbook for this alert (has to be configured while setting up alert). This key is omitted if the runbook isn’t configured- If the entity under alert has
tagsassociated with it, they are included in custom details astag_<tag_name>=true time_in_alert- Duration for which this alert was observed. E.g., 8 in 10 minutes.
Opsgenie
| Opsgenie field | Type | Description |
|---|---|---|
| message | string | Title for the incident |
| alias | string | Dedup key for the incident |
| description | string | Description of the alert. If a description is provided while configuring the rule, it appears here. Otherwise, this field is omitted |
| tags | array of strings | Tags associated with the entity |
| actions | array of strings | [“Debug”] |
| details | object | Described below |
| entity | string | null |
| source | string | Last9 Dashboard |
| note | string | A string description of the alert, along with the health dashboard link for the alert |
| responders | array of objects | Not used |
| visibleTo | array of objects | Not used |
| priority | string | Not used |
| user | string | Not used |
Details
alert_condition: Condition set on alert. Static alerts, it is of the format.expr > 10based on the threshold configured. For anomaly alerts, it is of the formatalgo_name(tunable, expr). For example, for a high spike alert set with tunable 3, this would behigh_spike(3, expr)algorithm: Type of alert (static_threshold,increasing_changepointetc)component:nulllast9_dashboard: Link to the health dashboard for this alertexpression: Name of the indicatorservice: Name and type of the entitysource: Dedup key for this incidententity_name: Entity nameentity_type: Entity typeentity_team: Entity team. IsNoneif not assignedentity_tier: Entity tier. IsNoneif not assignedentity_workspace: Entity workspace. IsNoneif not assignedentity_namespace: Entity namespace. IsNoneif not assignedseverity: Severity of the alert (breach/threat)notification_call: Whether this alert is sent for the first time or repeated (first/repeat)runbook: Link to the runbook for this alert (has to be configured while setting up alert). This key is omitted if the runbook isn’t configured
Webhook
| Field | Type | Description |
|---|---|---|
| routing_key | string | The full generic webhook URL generated in Last9. This is used to send alerts to your configured endpoint |
| event_action | string | The type of event. Can be trigger, acknowledge or resolve |
| dedup_key | string | Deduplication key for correlating triggers and resolves. The maximum permitted length of this property is 255 characters |
| payload.summary | string | A brief text summary of the event, used to generate the summaries/titles of any associated alerts |
| payload.source | string | The unique location of the affected system, preferably a hostname or FQDN |
| payload.severity | string | The perceived severity of the status the event is describing with respect to the affected system. This can be critical, error, warning or info |
| payload.timestamp | timestamp | The time at which the emitting tool detected or generated the event |
| payload.component | string | Component of the source machine that is responsible for the event, for example mysql or eth0 |
| payload.group | string | Logical grouping of components of a service, for example app-stack |
| payload.class | string | The class/type of the event, for example ping failure or cpu load |
| payload.custom_details | object | Additional details about the event and affected system |
| images | array of objects | List of images to include |
| links | array of objects | List of links to include |
Flock
Flock notifications use FlockML for rich formatting. When a webhook URL containing api.flock.com or flock.co is detected, Last9 automatically formats the payload for Flock.
| Field | Description |
|---|---|
| flockml | FlockML-formatted message containing all alert details |
The FlockML message includes:
- Event Type: TRIGGER or RESOLVED with emoji indicator
- Summary: Alert title with severity icon
- Severity: BREACH or THREAT level
- Component: Affected service or component
- Class: Type of alert (e.g., Static Threshold, SLO Breach)
- Timestamp: Formatted date and time
- Custom Details: Additional context (service, environment, etc.)
- Inspect Link: Direct link to view the alert in Last9
For detailed setup instructions, see the Flock Integration guide.
Google Chat
Google Chat notifications use the Cards v2 API for rich formatting. When a webhook URL containing chat.googleapis.com is detected, Last9 automatically formats the payload for Google Chat.
| Field | Description |
|---|---|
| cardsV2 | Array of Card objects with rich formatting |
Each card includes:
- Header: Alert summary with subtitle showing severity, class, and timestamp
- Sections: Organized alert details with decorated text widgets
- Button: “Inspect in Last9” link to view the alert
Severity Indicators
| Severity | Icon |
|---|---|
| Breach | 🔴 |
| Threat | 🟠 |
For detailed setup instructions, see the Google Chat Integration guide.
Telegram
Telegram notifications use HTML-formatted messages. When a webhook URL containing api.telegram.org is detected, Last9 automatically formats the payload for Telegram.
| Field | Type | Description |
|---|---|---|
| chat_id | string | The Telegram chat ID (from webhook headers) |
| text | string | HTML-formatted message content |
| parse_mode | string | Always “HTML” |
The message includes:
- Header: Event type (TRIGGER/RESOLVED) with severity icon
- Alert Details: Severity, component, class, timestamp
- Custom Details: Additional context fields
- Inspect Link: Direct link to Last9 dashboard
For detailed setup instructions, see the Telegram Integration guide.
Jira
Jira integration creates issues automatically when alerts are triggered. When a webhook URL containing atlassian.net is detected, Last9 formats the payload using Atlassian Document Format (ADF).
| Field | Type | Description |
|---|---|---|
| fields.project.key | string | Jira project key |
| fields.summary | string | Alert summary (max 255 chars) |
| fields.description | object | ADF-formatted description with alert details |
| fields.issuetype.name | string | Always “Task” |
| fields.labels | array | Labels including dedup key and “last9-automated-alert” |
| fields.priority.name | string | Mapped priority (if enabled) |
Priority Mapping
| Last9 Severity | Jira Priority |
|---|---|
| Breach | Highest |
| Threat | High |
Features
- Rich Description: ADF-formatted content with sections for alert details, custom fields, and raw JSON
- Automatic Labels: Dedup key and “last9-automated-alert” for easy filtering
- Resolution Comments: When alerts resolve, a comment is added to the issue
- Status Updates: Optionally transition issues to resolved status
- Deduplication: Only creates issues for first-time alerts (not repeats)
For detailed setup instructions, see the Jira Integration guide.
Zenduty
Zenduty notifications use a structured payload format for incident management. When a webhook URL containing zenduty.com is detected, Last9 automatically formats the payload for Zenduty.
| Field | Type | Description |
|---|---|---|
| title | string | Alert summary |
| alert_type | string | Severity level (critical, warning) or “resolved” |
| message | string | Alert summary text |
| summary | string | Detailed description of the alert |
| payload | object | Full alert payload with all context |
| urls | array | Link to view alert in Last9 Dashboard |
| entity_id | string | Deduplication key for correlating alerts |
Features
- Auto-Detection: URLs containing
zenduty.comare automatically detected - Rich Context: Includes severity, description, and dashboard links
- Alert Correlation: Uses
entity_idto correlate trigger and resolve events - Resolution Support: Automatically marks incidents as resolved when alerts clear
For detailed setup instructions, see the Zenduty Integration guide.
Troubleshooting
Please get in touch with us on Discord or Email if you have any questions.