Create a AWS STS Role
This tutorial walks through setting up a AWS STS (Secure Token Service) role for discovering resources via cloudwatch
Creating trusted role without external id
-
Visit AWS Console/Roles
-
Click Create Role
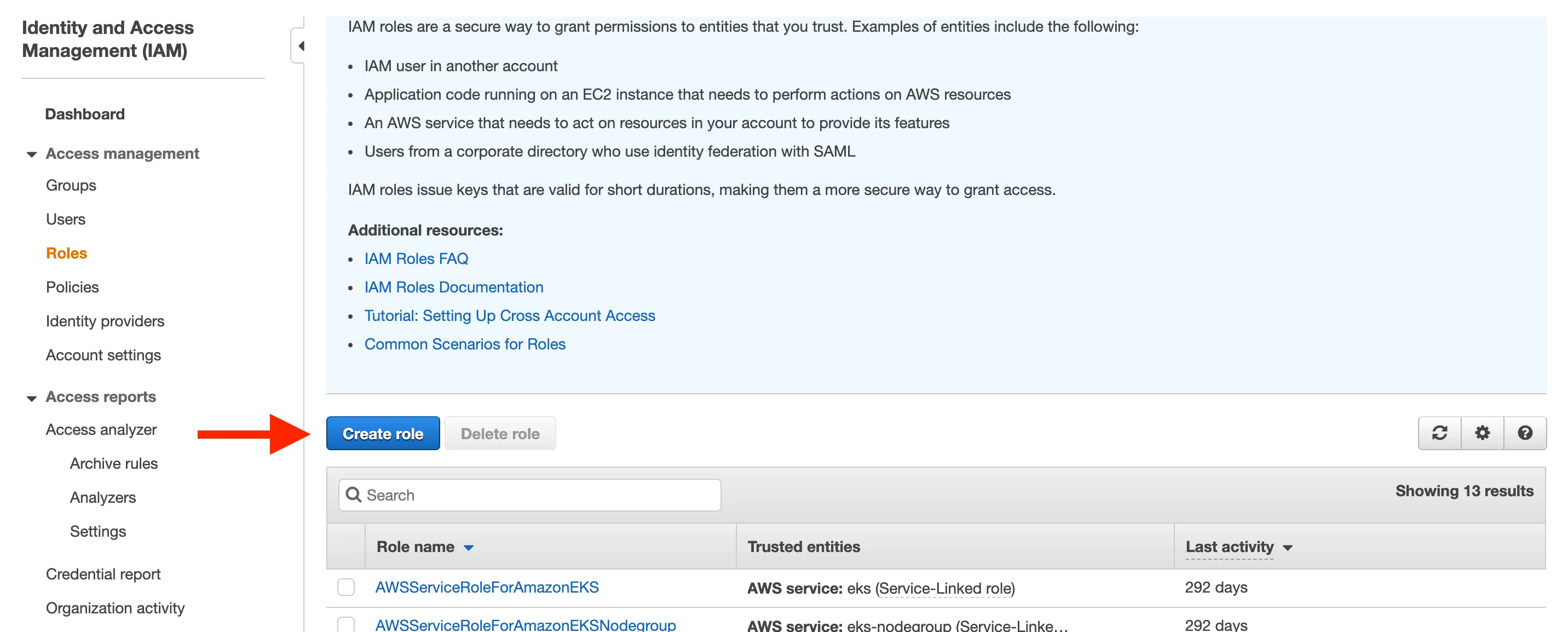
-
Select Another AWS Account tab
- Account ID:
652845092827 - Next Permissions
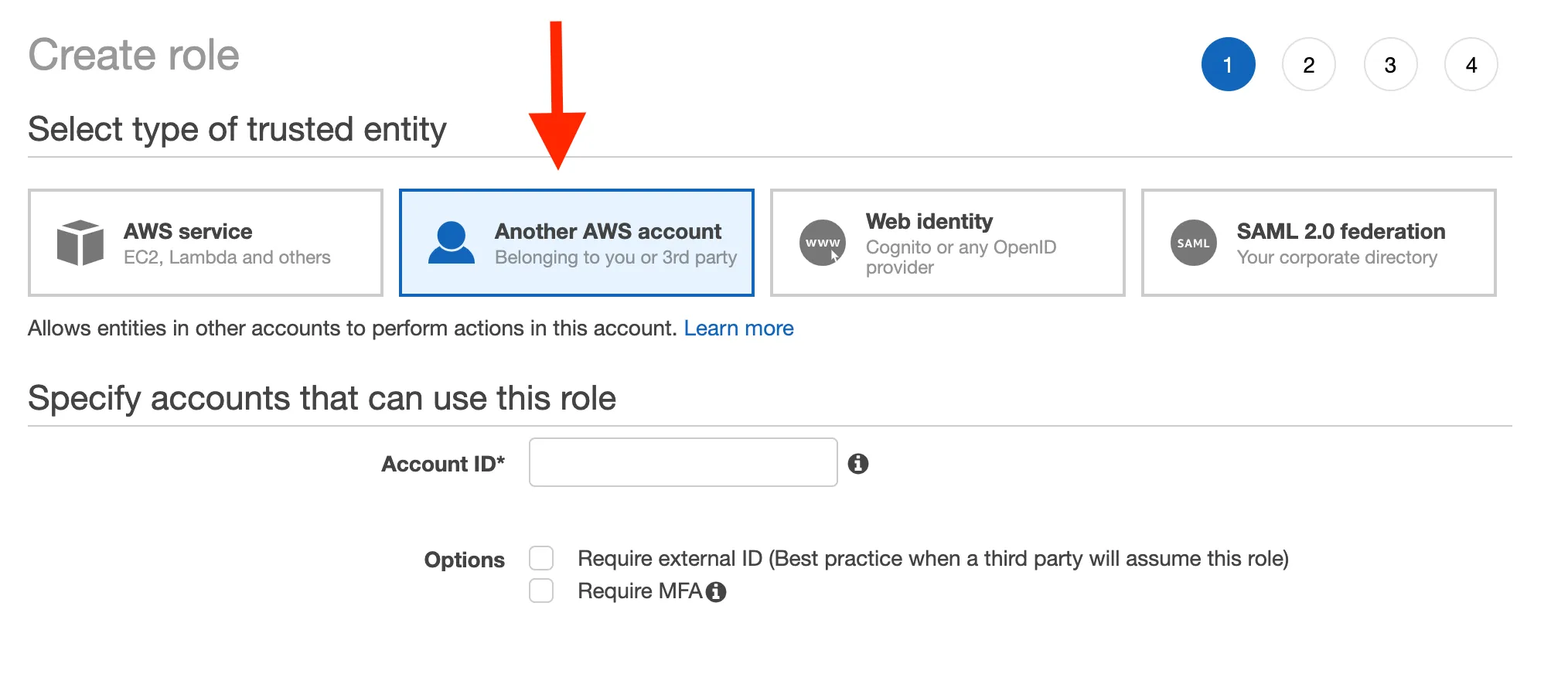
- Account ID:
-
Attach policies
a. SecurityAudit Policy
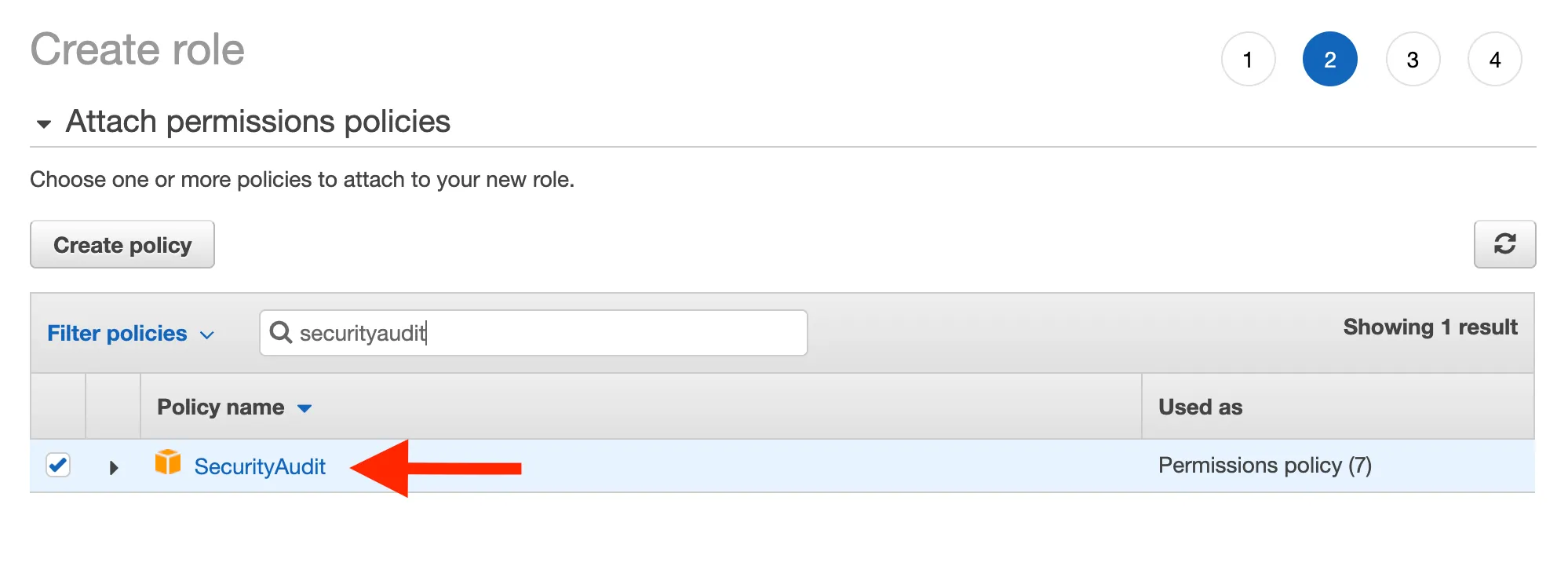
b. CloudWatchReadOnlyAccess Policy

c. Proceed to Next Steps
-
Add tags if needed
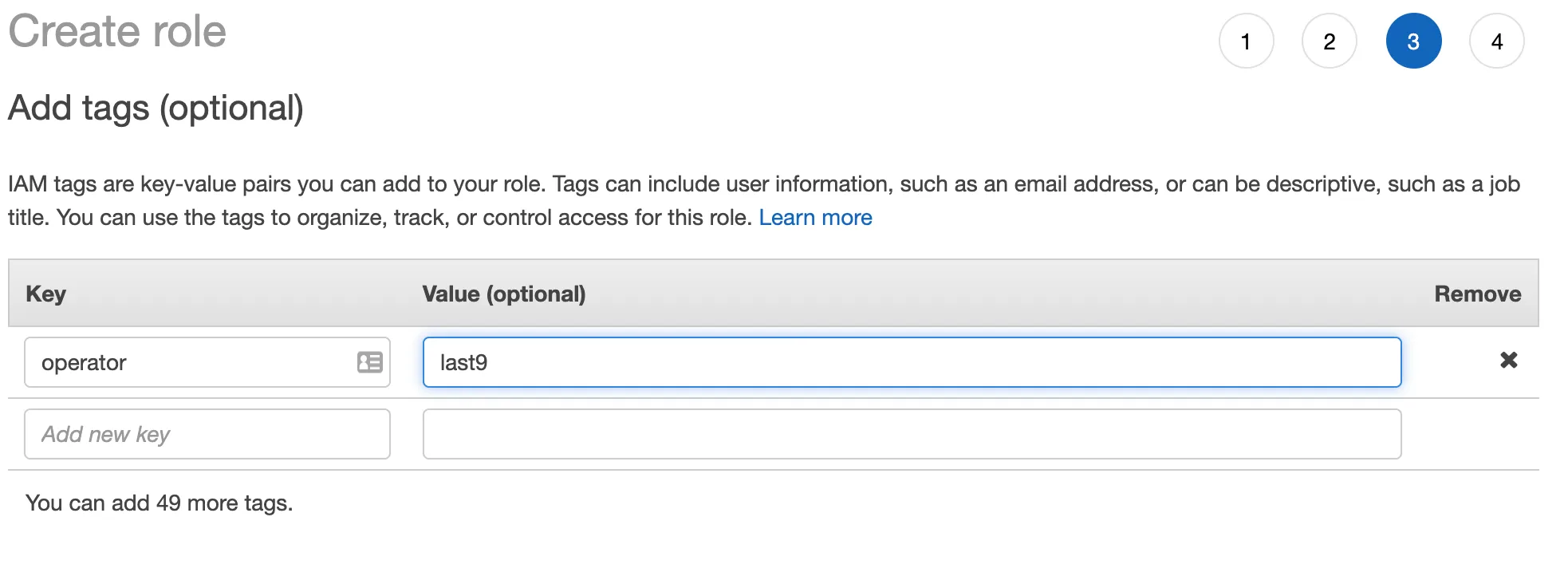
-
Review
- Role name:
${business_name}_last9_role - Role description: Security Audit Access to Last9
- Verify Last9 AWS Account Number
- Verify Granted Policy
- Create Role
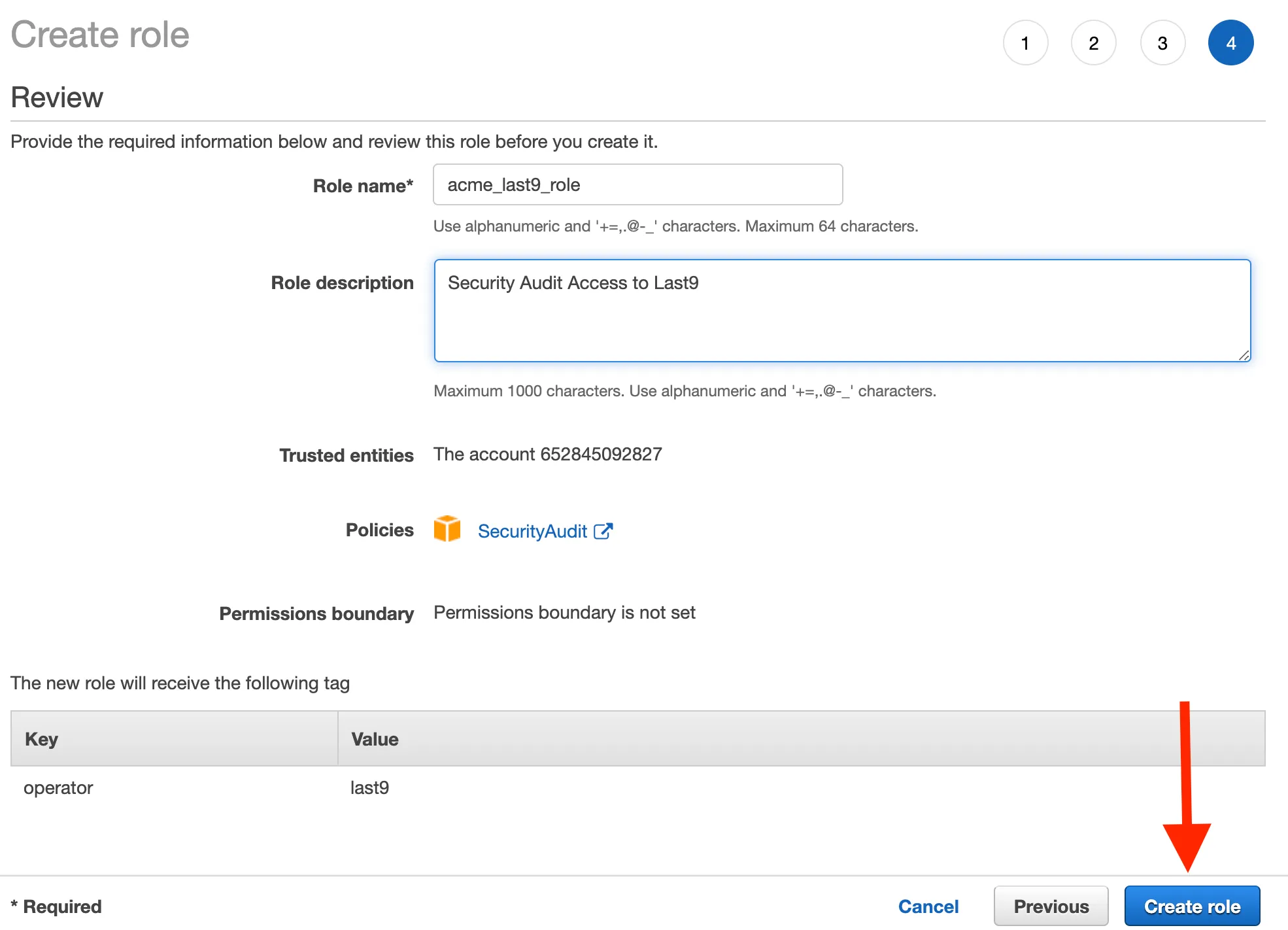
- Role name:
-
After the role is created, Go to Role → Trust Relationships → Edit Trust Relationship
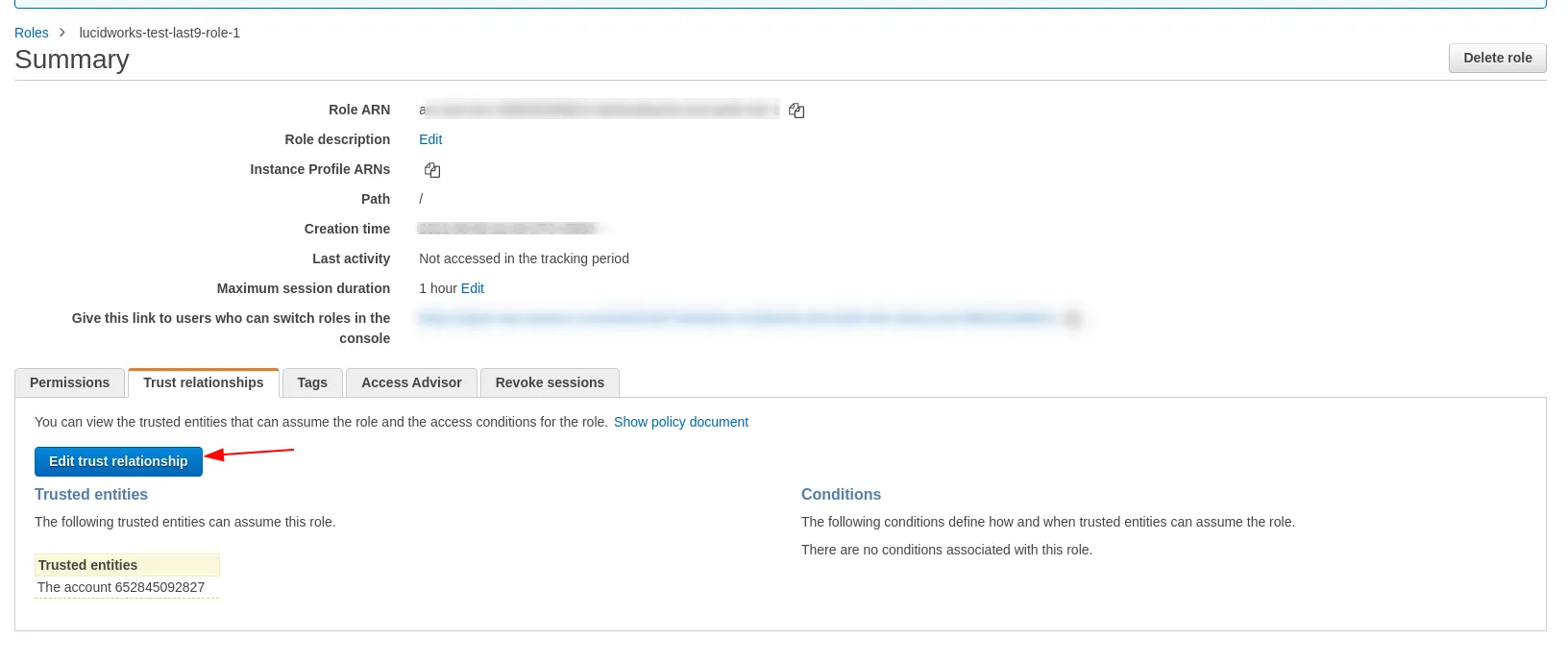
-
Update the JSON to the following and click “Update Trust Policy”
{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Principal": {"AWS": "arn:aws:iam::652845092827:root"},"Action": "sts:AssumeRole","Condition": {}}]} -
Edit the role and update “Maximum session duration” to 3 hours if your security policy permits it. Else leave it as 1 hour.

-
Share the created role ARN with your Last9 point of contact
Creating trusted role with external id
-
Visit AWS Console/Roles
-
Click Create Role

-
Select “Another AWS Account” tab with external ID as a random string. It has to be something other than “somerandomstring” and share it with Last9
- Account ID:
652845092827
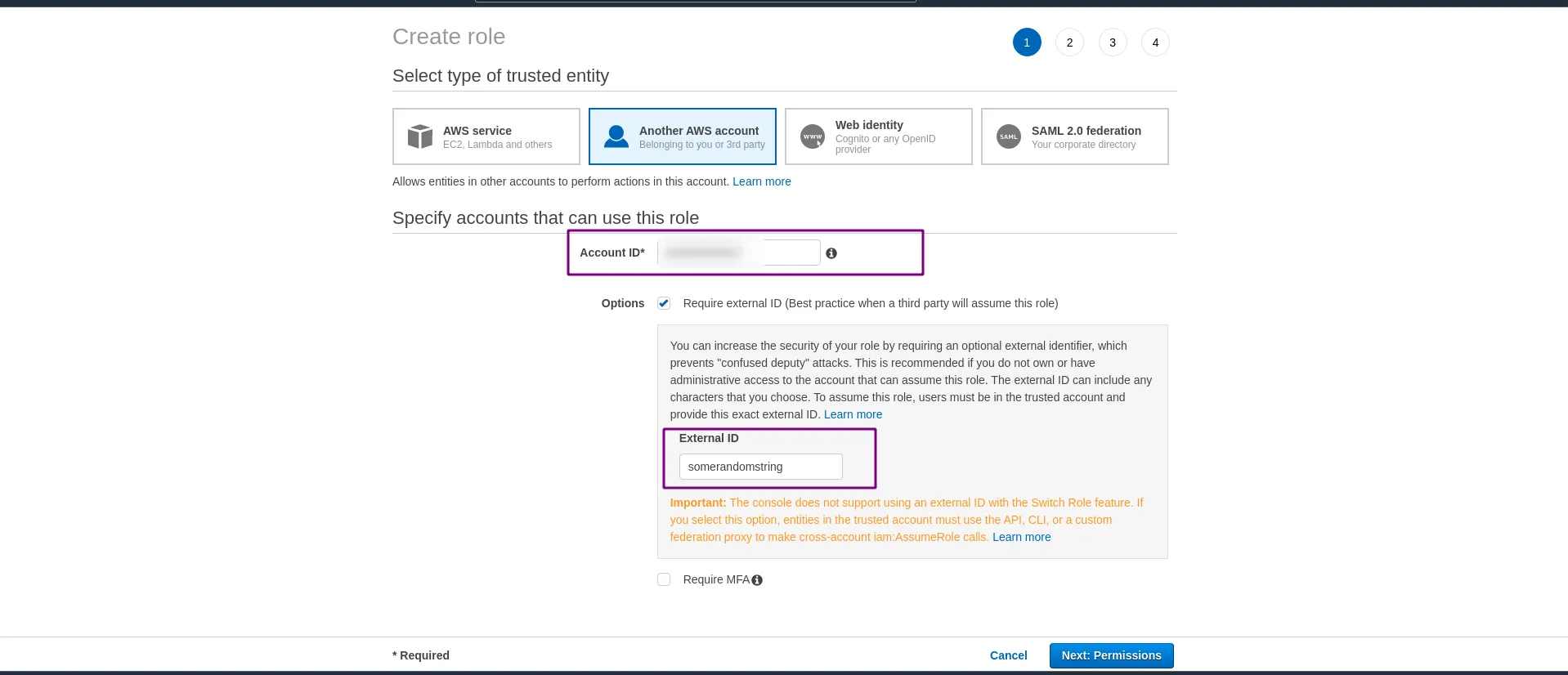
- Account ID:
-
Attach policies
a. SecurityAudit Policy

b. CloudWatchReadOnlyAccess Policy

c. Proceed to Next Steps
-
Add tags if needed

-
Review
- Role name:
${business_name}_last9_role - Role description: Security Audit Access to Last9
- Verify Last9 AWS Account Number
- Verify Granted Policy
- Create Role

- Role name:
-
After the role is created, Go to Role → Trust Relationships → Edit Trust Relationship

-
Update the JSON to the following and click “Update Trust Policy”. Ensure that the value for
sts:ExternalIdmatches the value set earlier for External-ID{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Principal": {"AWS": "arn:aws:iam::652845092827:root"},"Action": "sts:AssumeRole","Condition": {"StringEquals": {"sts:ExternalId": "somerandomstring"}}}]} -
Edit the role and update “Maximum session duration” to 3 hours if your security policy permits it. Else leave it as 1 hour

-
Share the created role ARN and external ID string with your Last9 point of contact