When you're managing Windows systems, one tool you’ll quickly come to appreciate is the Event Viewer.
It’s like a detailed diary of your system’s activities, giving you insight into everything that’s going on behind the scenes.
Whether you're diagnosing issues, keeping tabs on performance, or ensuring your system’s security, the event logs are your go-to resource.
For IT pros, knowing how to tap into these logs can make troubleshooting faster, save you time, and even help with stay on top of compliance.
What Are Event Logs in Windows?
Event logs in Windows are records of system events, including everything from hardware failures to software crashes. These logs capture system messages, warnings, errors, and informational events, offering insights into your system's behavior.
Windows logs events in a structured manner, allowing you to access them using the Event Viewer tool.
The logs are classified into different categories, which makes it easier to filter and search for specific data:
- Application logs: Events related to installed applications.
- System logs: Information about the operating system and its components.
- Security logs: These logs contain security-related events, including login attempts and account changes.
- Setup logs: Events related to the installation and setup of the system and software.
- Forwarded events: Logs collected from remote machines.
Each event entry in these logs contains a timestamp, event ID, level (such as critical or warning), and a description, making it easier to understand the context of an issue.
Key Components of Event Logs
Event logs are vital for tracking and troubleshooting activities within systems. Understanding their components can make it easier to navigate and analyze them.
Let’s break down the key components you’ll typically encounter:

Timestamp:
Every event in a log is timestamped, indicating the exact time the event occurred. This helps in tracking the sequence of events and identifying issues that happened at a specific point.
Event Type:
The event type describes what kind of event has occurred. It could be an error, warning, informational message, or success notification. Knowing the event type lets you prioritize issues based on severity.
Event Source:
The event source indicates which part of the system generated the log. Whether it’s a web server, database, or application service, the source helps pinpoint where things went wrong.
Message/Description:
This is the human-readable part of the log that explains what happened. It could be something like "Database connection failed" or "User logged in successfully." These messages are crucial for understanding the context of the event.
Event ID:
Some systems assign a unique identifier to each event. This helps reference specific events, especially when dealing with large sets of logs.
Severity Level:
Severity levels help categorize the event based on how critical it is. Common levels include Critical, Error, Warning, Information, and Debug. This component allows you to prioritize responses effectively.
User Information:
If the event involves a user (like logging in or performing an action), the log will often include details such as the user’s ID or username. This makes it easier to trace actions back to specific individuals.
Host or Device Info:
For systems with multiple servers or devices, the log will also include information about which host or device the event came from. This helps when managing distributed systems.
Why Event Logs Are Important
Event logs are crucial for several reasons:
Troubleshooting: They provide a detailed history of what happened before and after a problem occurred. This helps identify the root cause of system crashes, network failures, or application errors.
Performance monitoring: Logs show system health, indicating if resources are being strained or if specific components are not functioning properly.
Security: Event logs are an essential part of tracking security breaches or unauthorized access. By monitoring security-related events, IT administrators can spot potential threats early.
Compliance and auditing: Many businesses need to comply with regulations that require them to maintain and monitor logs for auditing purposes. Event logs help ensure compliance with standards like HIPAA, PCI DSS, or GDPR.
How to Access Event Logs in Windows
To begin working with event logs, you’ll need to access them through the Event Viewer, a built-in Windows tool.
Here’s how to open it:
- Press the Windows key and type "Event Viewer" in the search bar.
- Click on the Event Viewer app.
- Once opened, you’ll see the Event Viewer interface with several logs displayed in the left pane.
Here’s a quick breakdown of the main sections:
Windows Logs: This includes the default logs like Application, Security, Setup, System, and Forwarded Events.
Applications and Services Logs: Logs related to specific applications and services on your computer.
Custom Views: Custom filters that you can create to narrow down the log results to a specific time, severity level, or event type.
You can filter, sort, and search these logs based on different criteria to find exactly what you're looking for.
Types of Events in Windows Logs
Event logs contain different types of events, each with a specific purpose.
Here’s a quick look at the most common ones:
Information:
Information events are typically not an issue. These logs provide details about system activities or successful operations, such as software installation or system startup.
Warning:
Warning events don’t usually signify a problem, but they indicate that something may be off. For example, low disk space or a driver issue could generate a warning.
Error:
Error events are more serious. They suggest a problem with hardware, software, or services, such as a failed system update or application crash. These are critical to investigate.
Critical:
Critical events indicate a severe issue that can result in system instability or failure. Immediate attention is required when you encounter critical errors.
How do you Monitor and Analyze Event Logs
Once you've got your event logs in place, it's time to monitor and analyze them to ensure your system is running smoothly and to catch potential issues early.
Here’s how you can go about it:
Set Up Centralized Logging
Storing logs from various systems in one central location makes it easier to monitor and analyze. Tools like ELK Stack (Elasticsearch, Logstash, Kibana) or Last9 help aggregate logs from different sources into a single interface for streamlined management.
Real-time Monitoring
Keeping an eye on logs in real-time is crucial, especially when dealing with production environments. Real-time monitoring allows you to react quickly to critical events. Tools like Prometheus, Grafana, or Last9 can help you visualize logs live with customizable dashboards and alerts.
Log Parsing and Filtering
With logs generated in large volumes, it’s easy to get overwhelmed. Parsing and filtering logs by specific fields (like event type or severity level) help narrow down what’s important. Using tools like Fluentd or Logstash for parsing can simplify the process, ensuring you only see the most relevant data.
Threshold-Based Alerts
Set up alerts based on specific thresholds. For example, if the number of error logs exceeds a certain number in a minute, trigger an alert. This enables quick responses to issues before they escalate.
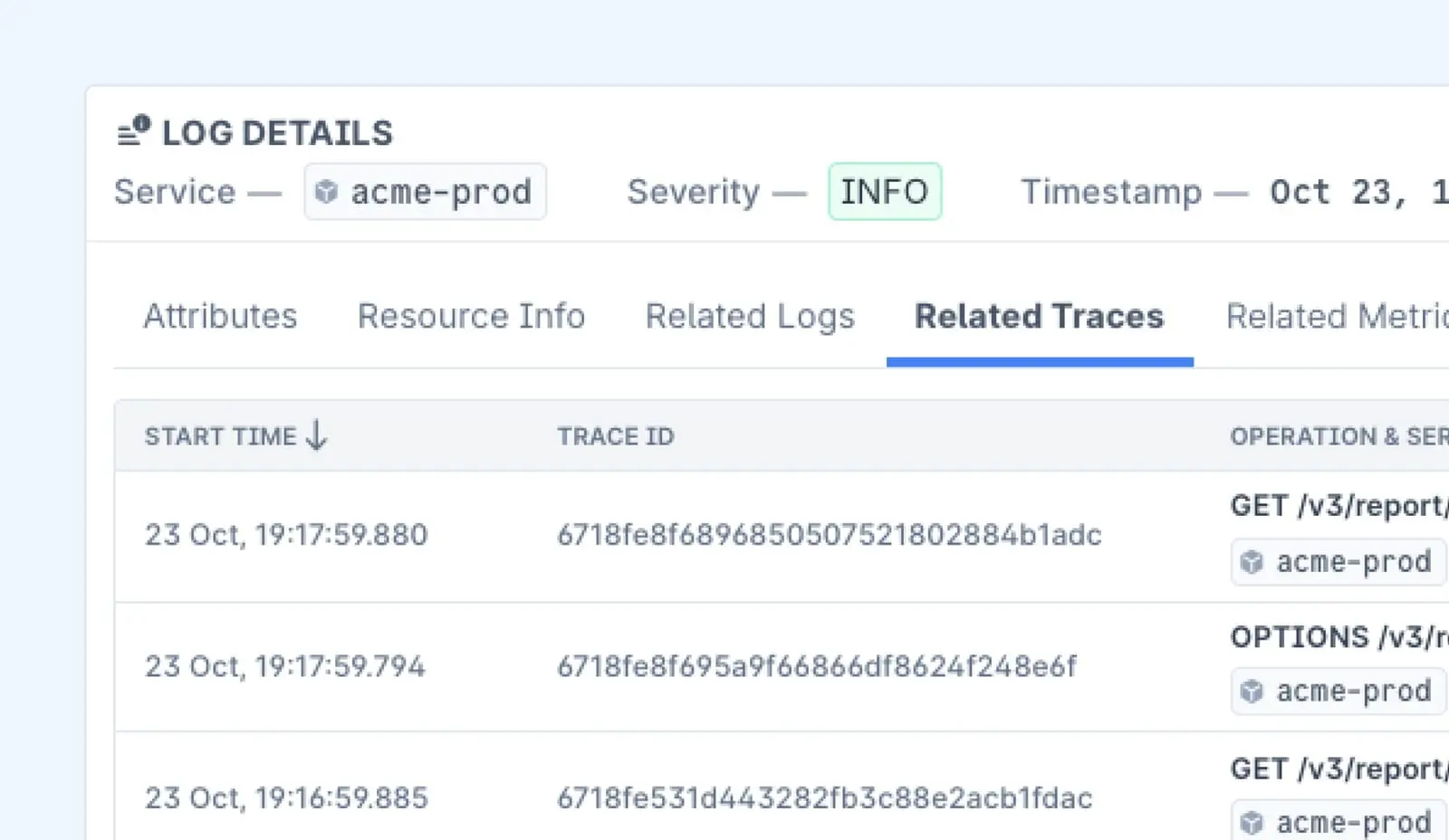
Log Correlation
Event logs don’t exist in a vacuum. Correlating logs across different systems can give you a clearer picture of what happened and why. If an error in your application is tied to a server issue, correlating logs can help identify the root cause.
Analyzing Patterns and Trends
Instead of only focusing on immediate issues, look for recurring patterns or long-term trends in your logs. Analyzing logs over time can reveal chronic problems, performance bottlenecks, or even security vulnerabilities.
Automated Log Analysis
Manual log analysis can be time-consuming, but automation can save you a ton of effort. Set up machine learning algorithms or rule-based engines to detect anomalies or patterns in logs automatically. This can help identify things like unexpected spikes in traffic or unusual error rates that might go unnoticed in a manual review.
Post-Mortem Analysis
After resolving an incident, it’s crucial to conduct a post-mortem analysis. Look through the logs from the event, track the timeline of the issue, and analyze how it was resolved. This helps in learning from the incident and preventing similar ones in the future.
How to Analyze Event Logs for Troubleshooting
Once you’ve accessed your event logs, it’s time to dig deeper and identify the root causes of issues.
Here’s a general approach for effective log analysis:
Use Event IDs
Each event in the log comes with a unique Event ID, which is a great starting point. You can search for these IDs online or refer to the Microsoft Event ID documentation to understand what the event means.
For example, Event ID 41 indicates that the system has rebooted unexpectedly, while Event ID 101 signals a problem with a service or application.
Check Event Details
Clicking on an individual event will show you more detailed information, including the exact error message, source, and sometimes even a solution or link to more resources. This can provide you with clues to address the issue directly.
Correlate with Other Logs
One event log might not provide enough information on its own. Check other logs to find correlations. For example, a critical error in the System log could be related to an application log entry showing a software crash.
Export Logs for External Analysis
If you're dealing with a particularly tricky issue, it might help to export your logs and analyze them in a different tool. You can export logs in CSV, XML, or EVTX formats and then use external programs or scripts for deeper analysis.
Why Automate Event Log Monitoring
While manually reviewing event logs is helpful, it can become tedious and time-consuming, especially in larger environments. To save time and catch problems earlier, consider using tools to automate event log monitoring.
Windows Performance Monitor
It allows you to set up alerts and create custom reports, making it easier to stay on top of system health without manually sifting through logs.
Log Management Solutions
Tools like Splunk, SolarWinds, and ELK Stack offer centralized log collection, search, and analysis. These tools provide more advanced filtering, visualization, and alerting features to streamline your monitoring process.
Syslog
If you're managing multiple Windows servers, consider forwarding event logs to a central syslog server. This can simplify management and analysis across your environment.
How to Use Windows Event Viewer
Windows Event Viewer is your go-to tool for managing and analyzing event logs on your system. It gives you insights into what's happening behind the scenes, helping you troubleshoot and stay on top of things. Here's how to make the most of it:
Accessing Windows Event Viewer
Opening Event Viewer
To get started, press Win + R to open the Run dialog, type eventvwr.msc, and hit Enter. Or, you can simply search for "Event Viewer" in the Start menu. Once it’s open, you’ll be greeted by a window with different types of logs waiting to be explored.
Navigating the Interface
The left panel is like your map to the logs. It has categories like Windows Logs, Applications and Services Logs, and Custom Views. These sections help you drill down into specific logs—like System, Application, or Security logs—depending on what you're looking for.
Viewing Event Logs
Choosing a Log
Pick a category, like Application or System, from the left panel to view the logs under that category. You’ll see a list of events with details like the time, event ID, and severity level—a history of what’s been going on.
Examining Event Details
When you click on an event, a window pops up with all the juicy details—Event ID, Source, Description, and more. This info is key for understanding what went wrong when it happened, and its impact.
Filtering Event Logs
Using Filters
Looking for something specific? Filters are your friend. You can narrow down logs based on event level, date/time range, event IDs, or even keywords.
To filter, right-click on a log category (like Application), select Filter Current Log, and set your filter parameters. This will save you time by focusing only on what matters.
Custom Views
Want to see logs based on custom criteria? You can create custom views to group logs that match specific conditions.
For example, set up a view to only show Error events from a certain source. To do this, click on Custom Views in the left panel, select Create Custom View, and define the filter conditions.
Saving Event Logs
Exporting Logs
Sometimes, you’ll want to save event logs for future reference or sharing. To do this, right-click the log category and select Save All Events As. You can choose to save it as an .evtx file for later review or even export it to a CSV for easier analysis in a spreadsheet.
Clearing Event Logs
Clearing Logs
Event logs can pile up, especially on busy systems. If you need to clear them, right-click on the log category (like Application or System) and select Clear Log. You'll be prompted to save them before clearing, in case you want to keep a backup.
Using Event Logs for Troubleshooting
Event Viewer is a great tool when troubleshooting issues like application crashes, security breaches, or hardware failures. Look out for error codes and descriptions in the logs—they’re often a helpful clue for solving the problem.
Keep an eye on warnings and error messages, and use event IDs to search online for targeted troubleshooting advice.
Best Practices for Event Log Management
To get the most out of your event logs, keep these best practices in mind:
Regularly Monitor Logs
Don't wait for a critical error to happen. Set up a routine to regularly review event logs and identify any emerging issues before they escalate.
Use Filters
Filters make it easier to focus on the most important logs, such as errors or critical events, without having to sift through the entire log.
Archive Logs
Event logs can grow quickly. Make sure to regularly archive older logs and set up automatic log rotation to keep things manageable.
Implement Alerting
Automate alerts for critical or error events so you can address problems immediately, rather than waiting for a user to report them.
Maintain Log Integrity
Ensure that event logs are protected from tampering, as they play a key role in security auditing.
Conclusion
Event logs in Windows are far from just a bunch of system messages—they’re an invaluable resource for monitoring, troubleshooting, and securing your system. Whether you’re keeping an eye on your system’s health or hunting down a pesky issue, logs are key.
If you're looking for a managed observability solution that simplifies all of this, Last9 is here to help.
We bring together metrics, logs, and traces into one unified view, making it easier for teams to connect the dots, stay on top of alerts, and troubleshoot more efficiently. Last9 integrates easily with tools like Prometheus and OpenTelemetry to enhance your monitoring experience.
Schedule a demo or try it for free to see how it works!



