In today’s world, cyber threats are getting more complex and tougher to spot, making it more important than ever for organizations to have a solid system in place to monitor, detect, and respond to security incidents.
SIEM (Security Information and Event Management) architecture plays a crucial role in this. If you’re trying to figure out how to design a SIEM system that works for your needs, you're in the right spot.
This guide will walk you through the key components of SIEM architecture, best practices, and a few lesser-known tips to help you set up your system like a pro.
What is SIEM Architecture?
SIEM architecture is the framework behind the system that collects, analyzes, and stores security data. These systems are crucial for spotting and responding to threats in real time by analyzing logs and events across your network, servers, and applications.
A good SIEM system offers centralized monitoring and even supports automated incident responses, helping to prevent or reduce security breaches before they escalate.
Key Components of SIEM Architecture
A solid SIEM architecture is made up of several key components.

Data Sources
The foundation of any SIEM system is the data it collects. This includes logs from things like firewalls, servers, routers, and intrusion detection systems. The more diverse and comprehensive your data sources, the stronger your overall security setup will be.
Data Collection
Once you've got your data sources lined up, the next step is pulling in the information. Data collection is usually done with agents or collector tools that grab logs from devices and systems across your network. Depending on your needs, this data can be collected in real-time or at set intervals.
Data Normalization
Not all the data you collect will come in the same format. SIEM systems need to normalize this data to make sure everything is consistent. This step is key for making it easier to analyze and correlate data from different sources, ensuring you're getting an accurate picture of what's going on.
Data Correlation
This is the heart of SIEM systems. Correlation helps you spot patterns that could indicate security issues.
For example, a bunch of failed login attempts from different locations could point to a brute-force attack. Correlating related events allows SIEM systems to reduce noise and help security teams focus on the real threats.
Event and Incident Management
Once data is correlated, it’s analyzed to create alerts for the security team. A strong SIEM system offers both automated responses—like blocking a suspicious IP—and manual incident management features, helping security personnel act quickly when something’s off.
Reporting and Dashboards
Having a real-time dashboard that shows what’s happening in your security environment is critical. Detailed reports help you analyze trends, track attack vectors, and find system weaknesses.
Dashboards can be customized to focus on the risks most relevant to your organization, so your security team can stay ahead of emerging threats.
Storage and Retention
Security data needs to be stored securely for future use and compliance. SIEM systems often use high-performance databases, but as data volumes increase, many are turning to cloud-based or distributed storage solutions for the scalability they offer.
SIEM Hosting Models
Choosing the right hosting model for an SIEM (Security Information and Event Management) system is key to its effectiveness. It impacts the control, scalability, and cost-efficiency of your security infrastructure.
There are three primary hosting models for SIEM systems: self-hosted, cloud-based, and hybrid solutions.
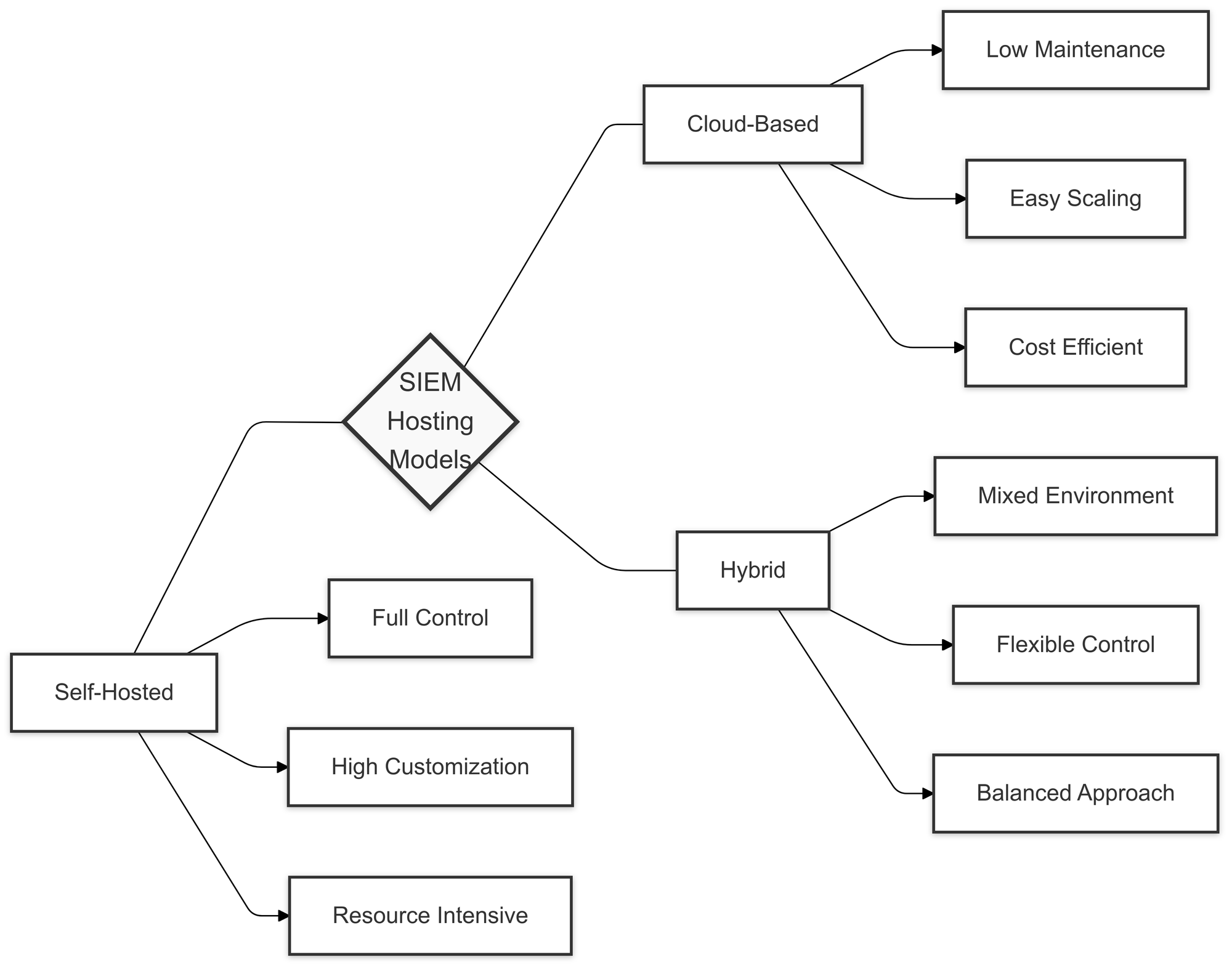
Here’s a breakdown of each:
Self-Hosted SIEM
A self-hosted model gives you full control over hardware, software, and data. This option offers deep customization and is often chosen by organizations with strict security requirements. However, it comes with more management responsibilities, including maintenance, updates, and scaling—tasks that can be resource-intensive.
Cloud-Based SIEM
With a cloud-based SIEM, the service provider takes care of the infrastructure and scaling. This model is great for businesses seeking flexibility, lower maintenance overhead, and an easily scalable solution. It’s especially suited for organizations that want to harness the cloud’s benefits while keeping upfront costs low.
Hybrid SIEM
Hybrid solutions mix the best of both worlds, combining on-premises and cloud-based components. This model lets organizations keep sensitive data on-site while taking advantage of cloud scalability and processing power. Hybrid SIEMs are ideal for businesses with complex security needs that need both flexibility and control.
Each hosting model offers its own set of benefits. The best option depends on your organization’s size, regulatory requirements, and available resources.
How Does Compliance and Security Management Work in SIEM
Compliance and security management go hand in hand, ensuring systems stay secure while meeting industry regulations. SIEM (Security Information and Event Management) systems simplify both tasks by blending powerful analytics with automation. Here’s how:
Tracking Compliance Requirements
SIEM systems help track and report on compliance standards like HIPAA, GDPR, and more. They collect and analyze logs from various sources to generate audit trails, making it easier for organizations to meet required regulations.
Security Data Analytics
With real-time monitoring and event correlation, SIEM systems spot potential threats before they escalate. Automated alerts are triggered when suspicious activity is detected, enabling rapid responses and reducing the likelihood of a breach.
Unified Approach
Instead of juggling separate tools for security monitoring and compliance tracking, SIEM systems offer a single platform for both. This integrated approach helps organizations stay on top of requirements and manage risks effectively.
In short, SIEM systems streamline compliance and security management, allowing organizations to stay secure and compliant without the hassle of handling multiple processes.
SIEM Logging Process
Logging is the core function of any SIEM (Security Information and Event Management) system. It collects and analyzes data from various sources to identify potential security threats.
The logging process includes key aspects like log retention, flow, and management to ensure effective data handling.
Here’s how it works:
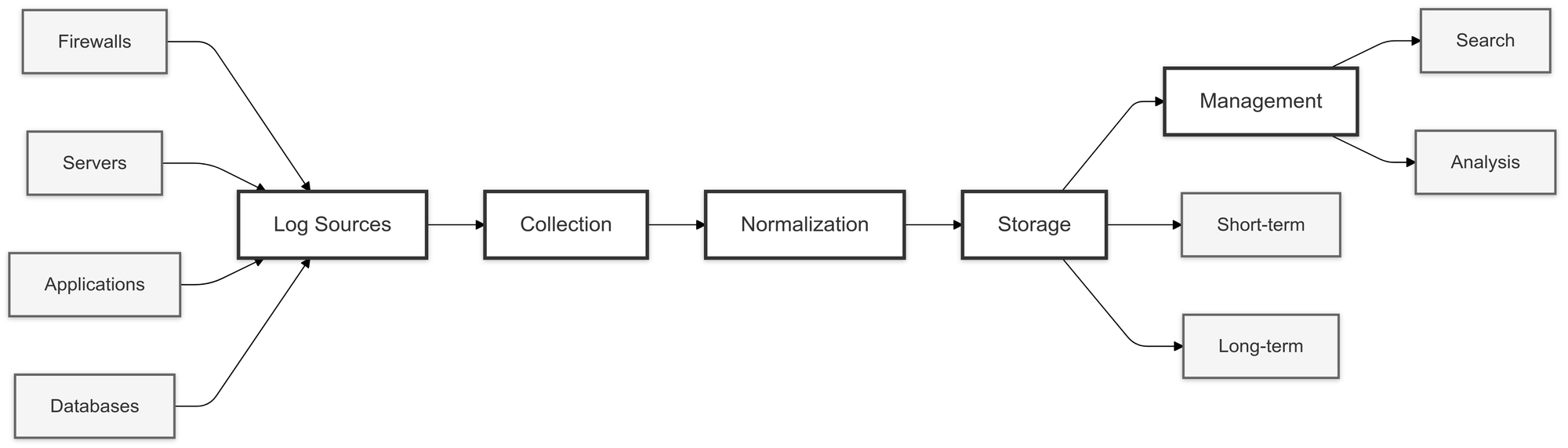
Log Collection and Flow
SIEM systems gather logs from diverse sources such as firewalls, servers, applications, and databases. These logs are aggregated and normalized to ensure consistent formatting, making analysis and correlation easier. This data flow is continuous, ensuring that all relevant events are captured in real time.
Log Retention
Retaining logs is crucial for compliance and forensic investigations. SIEM systems offer configurable retention policies, allowing organizations to store logs for the required duration based on regulatory needs or internal policies. Logs may be retained for days, months, or even years, depending on the data's importance.
Log Management
Effective log management ensures logs are easily searchable, accessible, and secure. SIEM systems offer features like indexing and categorization to help security teams quickly locate logs during investigations. Logs are often encrypted to protect sensitive data from unauthorized access.
How to Size and Scale Your SIEM System
Sizing an SIEM (Security Information and Event Management) system is crucial to ensure it meets the demands of your organization’s security environment.
The right setup needs to account for various factors, including data volume, velocity, hardware resources, and storage needs.
Scalability is another key factor, as your system should grow alongside your organization. Here’s a breakdown of the main considerations:
Velocity and Volume of Data
The first thing to consider is how much data your SIEM will need to process.
- Volume refers to the total amount of logs and events generated by your systems.
- Velocity refers to how quickly this data is generated.
High-velocity environments, like those with numerous active users or devices, will require a more powerful SIEM system to process and analyze the data in real-time.
Hardware Requirements
The hardware needed for a SIEM system depends on the data volume and velocity.
- Self-hosted systems require robust servers with sufficient CPU, RAM, and network bandwidth to manage large incoming data streams.
- Cloud-based systems have the hardware managed by the provider, but understanding resource requirements is still essential for scalability.
Storage Needs
Long-term log storage is necessary for both compliance and analysis, requiring ample storage space.
- The amount of storage you need depends on your retention policy and the volume of data generated.
- For organizations with strict compliance standards, logs may need to be stored for several years. Scalable storage options, like cloud storage or dedicated on-prem solutions, should be planned accordingly.
Scalability Options
Scalability ensures that your SIEM system can expand as your needs grow.
- Cloud-based and hybrid SIEM systems are generally easier to scale, automatically adjusting resources as needed.
- For self-hosted systems, scalability requires careful planning, as adding resources (such as servers or storage) can be complex.
The Role of Threat Intelligence in SIEM Architecture
While many SIEM systems can handle standard correlation and analysis, integrating threat intelligence feeds can elevate your system to a whole new level.
Threat intelligence provides crucial context, such as known attack signatures or IP addresses tied to cybercriminals.
Combining internal data with external threat intelligence helps SIEM solutions spot sophisticated attack patterns more effectively, enabling security teams to respond faster.
Lesser-Known Insights into SIEM Architecture
Distributed SIEM Systems
Traditional SIEM systems often work in a centralized setup, but there's growing interest in distributed SIEM architecture. This approach spreads data collection and analysis across multiple nodes within the organization’s network.
Distributed SIEM systems offer better scalability, reduce latency, and ensure quicker event processing—especially in large enterprises with complex infrastructures.
Machine Learning and SIEM
Advanced SIEM platforms are increasingly incorporating machine learning algorithms to improve threat detection.
Machine learning models can sift through vast amounts of historical security data, identifying patterns and flagging anomalies that traditional methods might miss. As cyber threats evolve, this added layer of proactive security can make a real difference.
Cloud-Native SIEM Solutions
With more organizations moving to cloud environments, cloud-native SIEM systems are becoming a popular choice. These solutions are specifically designed to handle the scale and complexity of modern cloud infrastructure.
They integrate seamlessly with cloud services and can manage the large volumes of data generated by cloud-based applications and platforms.
SIEM as a Service (SIEMaaS)
An increasingly popular trend is SIEM as a Service (SIEMaaS), where organizations outsource the management of their SIEM systems to third-party providers. This model helps reduce the burden of setting up and maintaining the system.
SIEMaaS providers offer services like data collection, analysis, reporting, and incident response, providing scalability and flexibility for businesses of all sizes.
Conclusion
Building a solid SIEM architecture isn’t a one-size-fits-all solution. It requires thoughtful planning, a clear understanding of your organization's unique security needs, and a commitment to continuous improvement.
While the key components and best practices we've covered will set you on the right path, always keep in mind that the threat landscape is in constant flux.



