In today’s connected world, network device monitoring plays a vital role in ensuring reliable performance and reducing downtime. Monitoring devices like routers and switches helps detect issues early, improve efficiency, and keep operations running smoothly.
This guide breaks down the basics of network device monitoring and explains why it’s a critical part of effective network management.
What is Network Device Monitoring
Network device monitoring is the process of continuously tracking the health, performance, and activity of devices like routers, switches, and access points within a network.
It helps ensure these critical components operate efficiently, detect issues early, and maintain network reliability.

Observability vs. Telemetry vs. Monitoring
Why Is It Important?
Think of your network as a bustling highway system. Each router, switch, and access point is like a critical intersection. When one breaks down, the ripple effects can be massive.
Network device monitoring ensures that these critical components are always in top shape by:
Minimizing Downtime
Early detection of issues means you can fix problems before they escalate.
Optimizing Performance
Monitoring helps identify underperforming devices and improve their efficiency.
Enhancing Security
Continuous tracking can flag unusual activity, helping to prevent breaches.
Supporting Growth
As your business scales, monitoring ensures your infrastructure grows without hiccups.

Key Components of Network Device Monitoring
So, what exactly goes into monitoring network devices? Here’s a breakdown of the essentials:
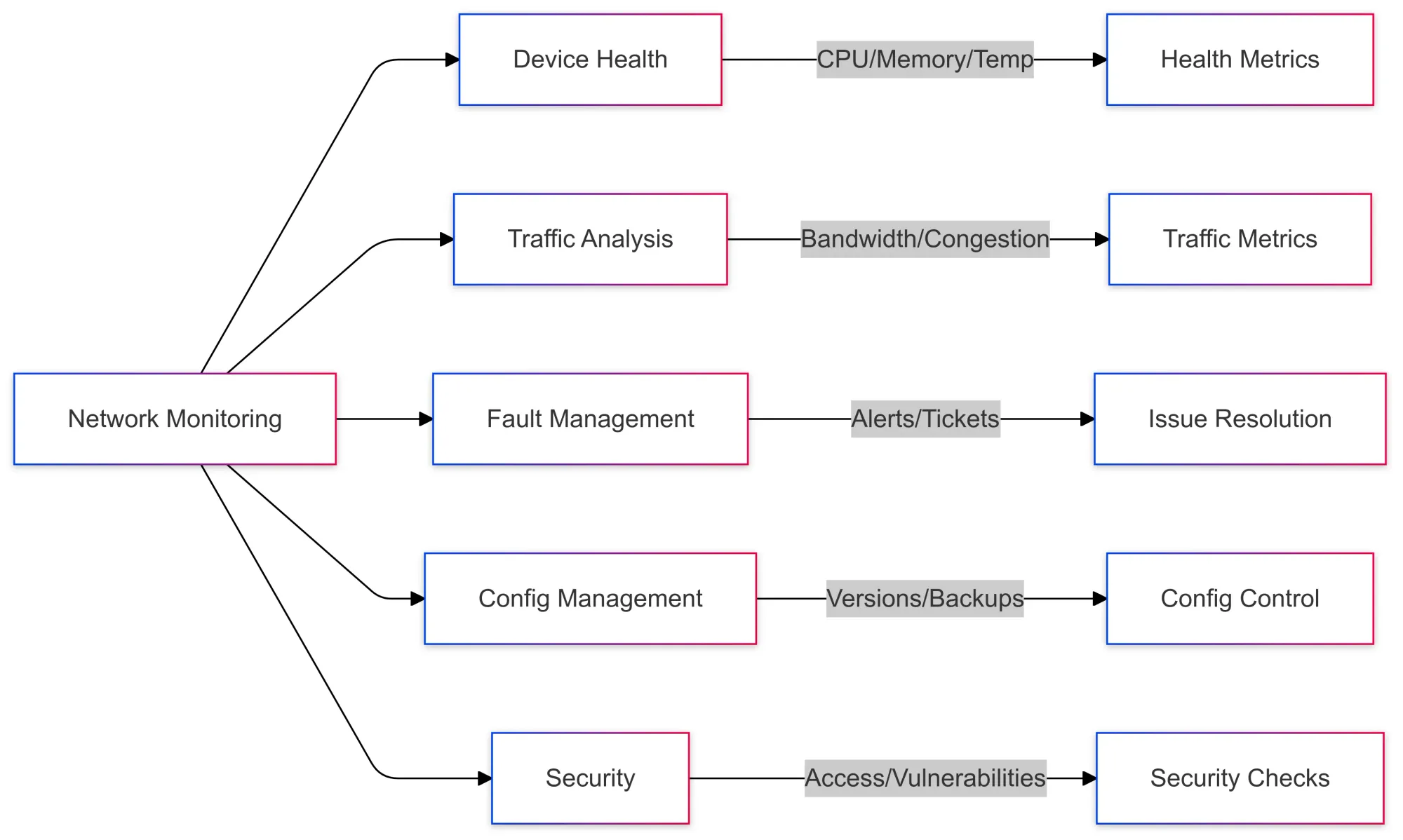
1. Device Health Monitoring
This involves keeping tabs on the status of devices like routers, switches, and firewalls. Metrics such as CPU usage, memory utilization, and temperature can indicate if a device is close to failure.
2. Traffic Analysis
Understanding how data flows through your network is crucial. Monitoring tools analyze traffic patterns to identify congestion, bandwidth hogs, or unusual spikes.
3. Fault Management
When things go wrong, quick action is key. Fault management involves detecting issues and sending alerts to ensure they’re resolved swiftly.
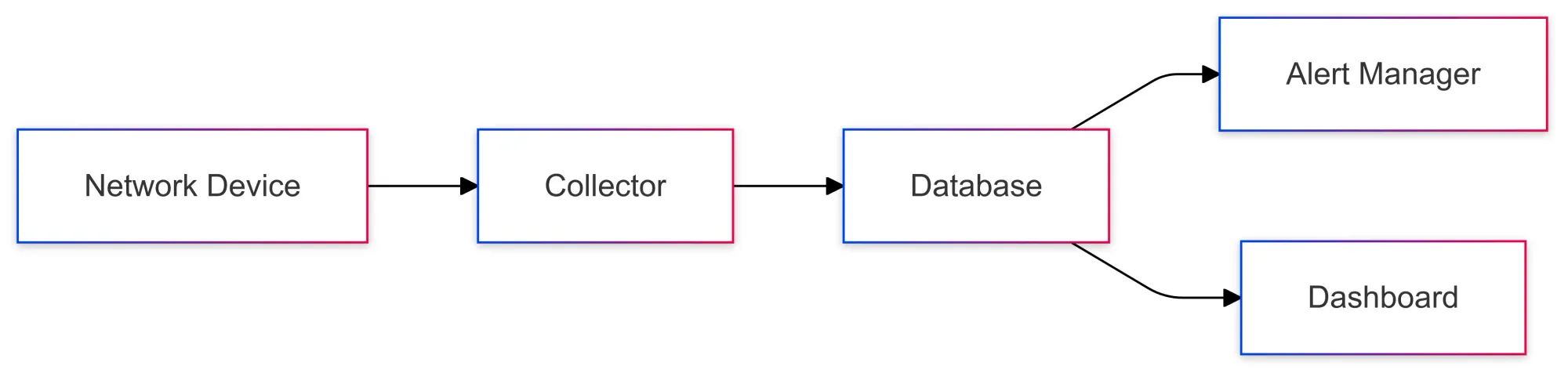
4. Configuration Management
Tracking changes in device configurations ensures consistency and helps roll back unwanted changes.
5. Security Monitoring
Monitoring devices for unauthorized access, vulnerabilities, and anomalies keeps your network safe.
How to Correlate Device, Network, and Application Layers
Modern IT environments are interconnected webs of devices, networks, and applications.
Monitoring these layers in isolation can leave gaps, making troubleshooting or optimizing performance harder.
Here’s how correlating these layers can help:
1. Holistic Troubleshooting
You can trace issues across layers by viewing device, network, and application performance as interconnected. For example, an application slowdown might not be due to server performance but a network bottleneck.
2. Improved Root Cause Analysis
Correlation allows you to pinpoint where an issue starts. If an application crashes, monitoring data from devices and the network can reveal if it’s due to hardware failure, misconfigurations, or bandwidth limitations.
3. Enhanced Performance Tuning
Understanding how applications interact with network devices helps in fine-tuning performance. For instance, identifying latency between an app and a database server can guide network optimizations.
4. Unified Monitoring Platforms
Tools that integrate metrics, logs, and traces from all layers ensure nothing slips through the cracks. Unified platforms streamline monitoring, making it easier to correlate data and act swiftly.
Last9 has been an amazing partner in making inroads on what a solid observability platform should be. – Akash Saxena, CTO
How NetFlow Traffic Correlation Enhances Monitoring
Spotting Bandwidth Hogs
Imagine a sudden spike in network traffic. NetFlow correlation helps identify not just the source but also the type of traffic—say a misconfigured backup or a large file transfer. Armed with this insight, you can throttle or reallocate bandwidth to critical applications.
Detecting Anomalous Activity
NetFlow data can reveal traffic patterns deviating from the norm. For example, if a server starts sending data to an unusual IP address or over an odd protocol, it could signal malware or data exfiltration. Correlating this activity with other logs provides a clearer picture for swift action.
Pinpointing Latency Causes
Suppose users complain about slow application performance. NetFlow analysis can correlate traffic flows to reveal whether the issue lies with a specific network link, device, or application. This allows targeted troubleshooting without trial and error.

Why your monitoring costs are high
Validating QoS Policies
You’ve deployed Quality of Service (QoS) policies to prioritize critical traffic, like VoIP. NetFlow correlation lets you monitor whether VoIP packets are being prioritized and identify if non-critical traffic is consuming reserved bandwidth.
Understanding Inter-Datacenter Traffic
For organizations with multiple data centers, NetFlow correlation can show how much traffic flows between them and what kind. If replication traffic starts taking up too much bandwidth, you can schedule it during off-peak hours to avoid performance hits.
Identifying Rogue Devices
A previously unknown device suddenly shows up on the network, consuming significant bandwidth. Correlating NetFlow data with device details helps determine if it’s an authorized device or a rogue one needing immediate action.
Tracking DDoS Attacks
When a Distributed Denial of Service (DDoS) attack begins, NetFlow data correlation can identify the flood of incoming packets, the targeted services, and even patterns in the source IPs. This allows quicker mitigation by applying filters or blocking specific IP ranges.
Visualizing Traffic Trends Over Time
NetFlow correlation can aggregate data to identify trends, like the rise in cloud-based app usage or shifts in peak traffic hours. This helps with capacity planning and ensures resources are allocated effectively.
Enhancing Network Segmentation
By correlating NetFlow data, you can ensure that sensitive systems only communicate with authorized devices. For instance, if a database server is accessed from an unexpected subnet, it’s an indicator to tighten security rules.
Validating Post-Change Impact
After implementing changes—like routing updates or policy tweaks—NetFlow correlation can confirm if traffic is flowing as expected and highlight any unintended consequences, such as increased latency or traffic drops.

OTEL Collector Monitoring: Best Practices & Guide
How to Automate Device Discovery in Network Monitoring
Automated device discovery is the process of identifying and cataloging devices connected to a network without manual intervention.
Here are some common techniques used for automated discovery:
1. Simple Network Management Protocol (SNMP)
How It Works: SNMP queries devices using management information base (MIB) data to gather details like device type, status, and configuration.
Use Case: Widely used for discovering routers, switches, and other network devices that support SNMP.
Pros: Efficient for large networks.
Cons: Requires devices to have SNMP enabled and configured.
2. Address Resolution Protocol (ARP) Scans
How It Works: The discovery tool sends ARP requests to all IP addresses in a subnet to identify devices that respond.
Use Case: Detects devices actively communicating on a local subnet.
Pros: Lightweight and fast.
Cons: Limited to the local network; cannot cross subnets.
3. Network Scanning with Ping Sweeps
How It Works: Tools send ICMP (ping) requests to a range of IP addresses. Devices that respond are considered active.
Use Case: Basic technique for identifying live devices on a network.
Pros: Simple to use.
Cons: Misses devices with firewalls blocking ICMP.
4. Link Layer Discovery Protocol (LLDP)
How It Works: LLDP-enabled devices advertise their identity and capabilities on the network. Discovery tools listen to these broadcasts.
Use Case: Common in enterprise environments for discovering switches and routers.
Pros: Provides detailed information, such as device names and capabilities.
Cons: Limited to LLDP-compatible devices.
5. NetFlow and sFlow Analysis
How It Works: Monitors network traffic flows to identify devices communicating on the network.
Use Case: Detects both internal and external devices.
Pros: Effective for passive discovery.
Cons: Requires flow-enabled devices and may not capture all devices.

Top 5 Open Source SIEM Tools for Security Monitoring
6. DHCP Lease Monitoring
How It Works: Monitors the DHCP server for leases issued to devices.
Use Case: Tracks new devices as they connect to the network.
Pros: Automatically logs newly connected devices.
Cons: Devices with static IPs may be missed.
7. DNS-Based Discovery
How It Works: Queries DNS records for known device hostnames and IP addresses.
Use Case: Works well in networks with consistent DNS naming practices.
Pros: Lightweight and non-intrusive.
Cons: Relies on accurate DNS entries.
8. Cloud-Based APIs and Integrations
How It Works: Integrates with cloud providers or third-party systems (e.g., AWS, Azure) to discover devices.
Use Case: Identifies virtual machines, cloud-hosted resources, and SaaS devices.
Pros: Ideal for hybrid or cloud-native environments.
Cons: Requires API access and configuration.
9. Agent-Based Discovery
How It Works: Agents installed on devices report details back to a central system.
Use Case: Monitors both on-prem and remote devices.
Pros: Provides detailed information, including performance metrics.
Cons: Requires agent installation and management.
10. Active Directory and LDAP Queries
How It Works: Queries Active Directory or LDAP to discover registered devices.
Use Case: Identifies devices managed within enterprise directories.
Pros: Efficient for environments using centralized directory services.
Cons: Limited to devices registered in the directory.
5 Popular Network Device Monitoring Tools
With countless tools available, choosing the right one can be daunting. Here are a few standouts:
1. Nagios
Known for its flexibility, Nagios offers extensive monitoring capabilities, from device health to application performance. Its open-source version is a great starting point.
2. Last9
Last9 simplifies observability by unifying metrics, logs, and traces in one platform. It provides deep insights into network performance and errors, simplifying troubleshooting and improving alert management.
With integrations like Prometheus and OpenTelemetry, Last9 offers a comprehensive view of your infrastructure.
3. Paessler PRTG
PRTG offers an all-in-one solution with sensors for devices, bandwidth, and even virtual environments.
4. Zabbix
An open-source powerhouse, Zabbix excels in scalability and detailed reporting.
5. Datadog
While primarily known for application monitoring, Datadog’s network monitoring features are powerful and integrate seamlessly with other parts of its platform.
Benefits of Path Visualization with Device Health Monitoring
Faster Troubleshooting
Combining path visualization with device health context gives you a complete picture of the network's flow and the devices along the path.
When an issue arises, you can pinpoint the exact location and identify the device causing it—no more needle-in-a-haystack searches.
Proactive Problem-Solving
Visualizing paths while monitoring device health simultaneously helps catch potential problems before they escalate. For example, spotting a device with high CPU utilization can prevent a bottleneck later.
Improved Root Cause Analysis
Network outages often involve multiple layers of complexity. With both path data and device health metrics, you can analyze interactions between devices and paths to understand not just what happened but why it happened.
Optimized Performance
Visualizing paths helps identify inefficient routing or overloaded links, while device health context ensures the devices themselves are functioning at their best. Together, they provide actionable insights to optimize both traffic flow and device performance.
Enhanced Team Collaboration
A clear, shared visualization of the network path and associated device health metrics simplifies communication between teams.
Whether it's the network, operations, or security team, everyone can see the same data and work together efficiently.
Simplified Change Management
Planning network changes becomes more straightforward with visibility into paths and device health. You can simulate changes, assess their impact on both traffic flow and device workloads and implement adjustments with confidence.

Why You Need Server Monitoring Tools
Reduced Downtime
Offering a dual perspective of network topology and device health allows teams to respond to issues more quickly and effectively, leading to less downtime and happier users.
Better Capacity Planning
Combining path visualization with device health metrics helps identify trends over time, allowing you to anticipate growth needs and plan for upgrades with accurate data on both network and device usage.
Best Practices for Network Device Monitoring
To get the most out of your monitoring efforts, follow these tips:
1. Define Clear Goals
Know what you want to monitor and why.
2. Set Realistic Thresholds
Avoid false alarms by fine-tuning alert levels.
3. Automate When Possible
Use automation to reduce manual tasks and improve response times.
4. Regularly Review and Update
Networks evolve—your monitoring strategy should too.
5. Train Your Team
Ensure your IT staff knows how to use monitoring tools effectively.
Conclusion
Network device monitoring is essential for keeping your business running smoothly in a connected world. With the right tools and practices, you can maintain a reliable network that meets future needs.
If you're looking for a reliable observability and monitoring solution, Last9 is the perfect fit. It simplifies your monitoring experience by bringing together metrics, logs, and traces into one unified view. This integration makes it easier for your team to connect the dots, manage alerts, and troubleshoot issues faster.
Schedule a demo to learn more or try it for free!
FAQs
1. What is network device monitoring?
Network device monitoring is the process of continuously tracking and managing the performance, health, and activity of devices like routers, switches, and access points within a network. It ensures these devices operate efficiently and helps detect issues early to maintain network reliability.
2. Why is network device monitoring important?
Network device monitoring helps minimize downtime, optimize device performance, enhance network security, and support infrastructure growth. It allows you to identify and address issues before they escalate, keeping your network running smoothly.
3. What devices are typically monitored in a network?
Commonly monitored devices include routers, switches, firewalls, access points, and servers. These devices play a key role in ensuring the flow of data and the overall performance of the network.
4. How does network device monitoring work?
Network device monitoring works by collecting performance data from devices, such as CPU usage, memory utilization, and network traffic. This data is then analyzed to identify potential problems, optimize performance, and ensure the devices are operating as expected.
5. What are the benefits of network device monitoring?
The key benefits of network device monitoring include improved network uptime, better performance optimization, early issue detection, enhanced security through real-time monitoring, and easier scalability as your network grows.
6. What tools are used for network device monitoring?
There are various tools available for network device monitoring, including popular options like Nagios, Last9, SolarWinds, Paessler PRTG, and Zabbix. These tools help monitor device health, track performance, and generate alerts for potential issues.
7. Can network device monitoring prevent security breaches?
Yes, network device monitoring can enhance security by continuously tracking device activity and detecting unusual behavior, such as unauthorized access or traffic spikes, which could indicate a potential security breach.
8. How does network device monitoring support business growth?
As your network scales, network device monitoring ensures your infrastructure grows without issues. It helps manage increased traffic and device load, ensuring that your network remains efficient and reliable as your business expands.
9. How can I get started with network device monitoring?
To get started with network device monitoring, choose the right tools for your network, define your monitoring goals, and set up monitoring for key devices. Regularly review monitoring reports and adjust thresholds as needed to ensure optimal performance.
10. How does network device monitoring help with troubleshooting?
Network device monitoring provides real-time data about device performance, which helps identify and isolate issues quickly. By having visibility into the health of devices and the network, you can troubleshoot problems more effectively and minimize downtime.