In network monitoring, maintaining smooth and uninterrupted performance is essential to ensuring business operations run without a hitch. One of the most trusted and widely used protocols to achieve this is SNMP (Simple Network Management Protocol).
Managing a small office network or overseeing a large, complex enterprise system, SNMP monitoring is key to tracking device health, spotting potential issues early, and enhancing overall performance.
In this guide, we’ll take you through the basics of SNMP monitoring, explain why it’s so important, and show you how to implement it effectively in your network infrastructure.
What is SNMP Monitoring?
SNMP stands for Simple Network Management Protocol, a protocol that allows devices like routers, switches, servers, printers, and other networked hardware to communicate status and performance information to a central monitoring system.
This communication helps network administrators keep tabs on their devices, troubleshoot problems, and optimize network performance.
SNMP is a request-response protocol that works in a client-server model. The SNMP manager (usually the monitoring tool) sends requests to the devices, known as SNMP agents, which then respond with the requested data.
The information can include a wide range of device metrics, such as CPU load, memory usage, network throughput, and error rates.
The Basics of Network Device Monitoring Explained
Key Benefits of SNMP Monitoring
Centralized Monitoring
SNMP enables centralized monitoring of various network devices. Whether managing a few devices or thousands, SNMP helps you collect data in one location.
This simplifies network management and troubleshooting. Instead of manually checking each device, an SNMP-enabled system automatically retrieves and displays key performance indicators.
Proactive Issue Resolution
SNMP monitoring allows network administrators to identify issues before they lead to downtime. Regularly monitoring performance metrics allows potential problems (like high CPU usage or increasing network errors) to be detected early. Early detection enables action before minor issues turn into major disruptions.
Scalability
As networks grow, monitoring complexity increases. However, SNMP is highly scalable, making it a great fit for both small and large networks. Whether you're managing a few devices or a large, distributed system, SNMP can handle the load and provide real-time insights across multiple locations.
Cost-Effective
Compared to other network monitoring solutions, SNMP is cost-effective. It uses standard protocols supported by most network devices, reducing the need for expensive proprietary solutions.
SNMP can be implemented with open-source tools or affordable commercial software, making it accessible to organizations of all sizes.

Why Cloud Security Monitoring is Crucial for Your Business
How Does SNMP Monitoring Work?
To understand how SNMP monitoring works, let’s break it down:
- SNMP Manager: This is the system that collects and analyzes data from the SNMP agents. It can be a dedicated server or a cloud-based solution that communicates with SNMP agents to gather performance metrics.
- SNMP Agents: These are software components running on network devices that collect and store data. They respond to requests from the SNMP manager, providing it with real-time data on device health and performance.
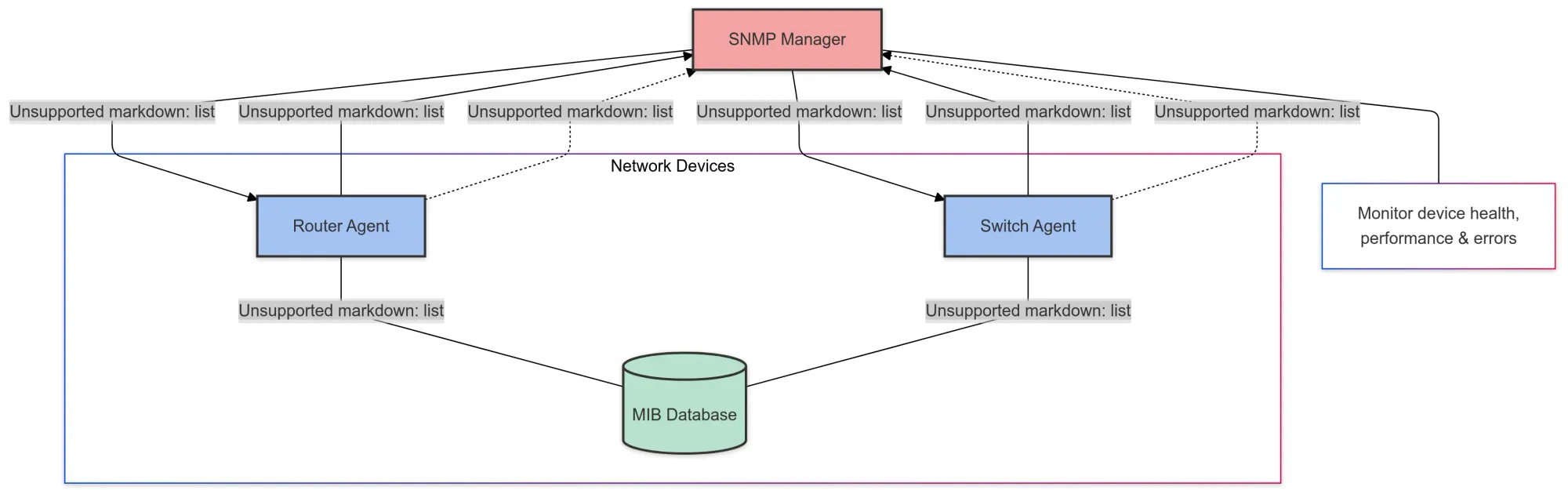
- Management Information Base (MIB): The MIB is a database that stores information about the devices being monitored. It defines the data that can be accessed, and organized into hierarchies of managed objects. Each managed object is identified by an OID (Object Identifier), which represents specific metrics or settings on the device.
- Trap Mechanism: In addition to the polling mechanism, where the manager requests data, SNMP also supports traps. Traps are unsolicited messages sent from SNMP agents to the manager, notifying it of events like critical errors, device reboots, or thresholds being exceeded.
Types of SNMP Monitoring
When it comes to SNMP monitoring, there are a few different approaches you can use, depending on your needs:
SNMP Polling:
This is the most common method of SNMP monitoring. The SNMP manager periodically polls the SNMP agents for updates on the status of network devices.
Polling intervals can be configured based on how often you want to retrieve updates. This approach ensures that the manager always has up-to-date information.
SNMP Traps:
SNMP traps are asynchronous messages sent by devices to alert the SNMP manager about certain events or threshold breaches. For example, if a router’s CPU usage exceeds a predefined limit, the SNMP agent will send a trap to notify the manager.
SNMPv3:
The latest version of SNMP, SNMPv3, introduces security features such as authentication and encryption to ensure that SNMP communications are secure. It’s particularly useful in environments where data integrity and confidentiality are top priorities.

DNS Monitoring: Everything You Need to Know
Key Components of SNMP and Their Roles in Network Monitoring
SNMP (Simple Network Management Protocol) relies on several core components to function effectively.
Each component has a specific role in gathering data, issuing commands, and ensuring network performance is properly monitored.
Let’s explore the key components of SNMP and how they contribute to network management.
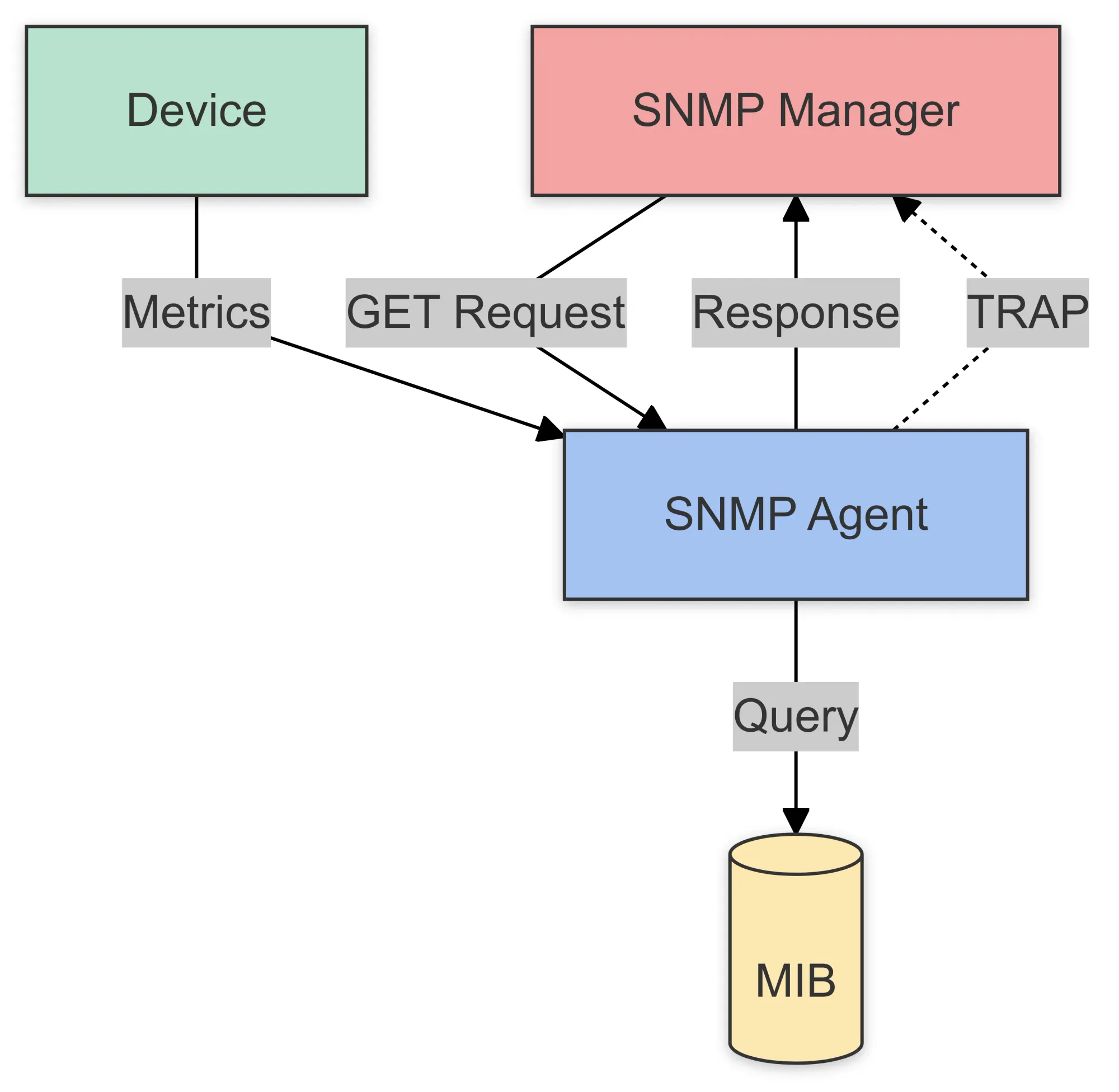
1. SNMP Manager
Role: Central Monitoring System
Description: The SNMP Manager is the system responsible for overseeing and managing the network. Often referred to as the “management station,” it runs the software that communicates with SNMP agents on network devices.
It collects data from the agents, sends requests for specific information, and sometimes even modifies the configuration of devices remotely.
Key Functions:
- Polls SNMP agents for specific information (using GET and GETNEXT commands).
- Receives and processes SNMP traps from agents, which notify it of important events or status changes.
- Stores and analyzes the data received from devices to provide insights into network health, performance, and issues.
- Manages the configuration of devices by sending SET commands to modify device parameters.
In Network Monitoring:
The SNMP Manager is the brain behind the monitoring system, orchestrating communication with agents to ensure devices are performing optimally. It typically includes dashboards and alerts, helping administrators stay informed about network status.
2. SNMP Agent
Role: Data Provider on Network Devices
Description: An SNMP Agent is a software component running on a network device (such as a router, switch, or server) that collects and stores information about the device's state and performance.
It acts as an intermediary between the SNMP Manager and the device, responding to requests for data and sending notifications about critical events.
Key Functions:
- Collects device data such as CPU usage, memory usage, and network throughput.
- Respond to requests from the SNMP Manager, providing requested data via GET or GETNEXT commands.
- Sends SNMP traps to the Manager when important events occur, such as high traffic, errors, or system reboots.
- Manages the MIB (Management Information Base), which is a collection of OIDs (Object Identifiers) representing device metrics and configuration settings.
In Network Monitoring:
The SNMP Agent provides the crucial performance metrics that the SNMP Manager uses to assess device health.
It enables network administrators to monitor a variety of devices and gain insights into their performance without needing to physically interact with each one.

API Monitoring: A Comprehensive Guide for Developers
3. Managed Devices
Role: Networked Equipment (Routers, Switches, Servers, etc.)
Description: Managed Devices are the physical or virtual devices on a network that are being monitored by the SNMP system.
These devices can include routers, switches, firewalls, servers, printers, and any other hardware that supports SNMP. Each device has an SNMP agent running on it that allows it to communicate its status and performance data to the SNMP Manager.
Key Functions:
- Provides data to the SNMP Agent about its performance, including metrics like uptime, error rates, traffic statistics, and resource usage.
- May receive configuration updates through SNMP SET commands sent by the SNMP Manager.
In Network Monitoring:
Managed devices are the "eyes and ears" of the network, continuously providing feedback about their own status. Their performance data is critical for detecting and troubleshooting issues such as bottlenecks, failures, or underperformance.
4. Management Information Base (MIB)
Role: Data Repository for SNMP
Description: The MIB is a hierarchical database used by SNMP agents to store information about a device's configuration and performance. It consists of a collection of OIDs (Object Identifiers), each representing a specific metric or device setting. The MIB defines the structure and type of data available from each managed device.
Key Functions:
- Defines the data model for SNMP communication, specifying what data can be requested or modified.
- Organizes device metrics into a tree structure that makes it easier for the SNMP Manager to query and retrieve data.
- Stores information like system uptime, interface statistics, and error rates, which can be retrieved using SNMP commands.
In Network Monitoring:
The MIB acts as the blueprint for what the SNMP Manager can monitor or configure on managed devices. It ensures that the data pulled from each device is consistent and structured.

A Beginner's Guide to GCP Monitoring
5. Object Identifiers (OIDs)
Role: Unique Identifiers for Data Points
Description: OIDs are unique identifiers used within the MIB to represent specific pieces of information about the managed device. Each OID corresponds to a particular metric, such as device uptime or network interface status.
Key Functions:
- Represents individual data points in the MIB, making it easy to retrieve specific information.
- Ensures structured communication between the SNMP Manager and agents, so each request or response targets the correct data.
In Network Monitoring:
OIDs are the primary way that data is organized in SNMP systems. For example, if you want to monitor the CPU load on a device, you would query the OID associated with that metric in the device’s MIB.
How These Components Work Together
To summarize the interaction between these components in network monitoring:
- The SNMP Manager sends a request to an SNMP Agent on a Managed Device, asking for a specific piece of information (such as memory usage).
- The SNMP Agent checks the MIB for the relevant OID, retrieves the corresponding data, and sends it back to the manager.
- The SNMP Manager then processes the received data, displays it to the network administrator, and may generate alerts or reports based on the metrics collected.
- If an issue is detected, the SNMP Manager can send a SET command to modify the configuration of the device or issue a TRAP command to notify the administrator of a critical event.

Proactive Monitoring: What It Is, Why It Matters, & Use Cases
Core SNMP Commands and Their Applications
In SNMP (Simple Network Management Protocol), the fundamental commands are used to interact with network devices, retrieve data, and configure settings.
These commands allow SNMP managers (the monitoring system) to communicate with SNMP agents (devices like routers, switches, and servers) to gather information and manage network performance.
Here’s an overview of the core SNMP commands and their applications:
1. GET
Command: GET
Application: The GET command is used by the SNMP manager to request specific information from an SNMP agent. This command is typically used to retrieve a single value from a device, such as CPU usage, memory utilization, or network traffic data.
Example Use:
A network administrator may use the GET command to fetch the current CPU load from a router or switch.
How it works: The SNMP manager sends a request for a specific Object Identifier (OID) that represents the metric or data point it wants. The agent responds with the current value of that OID.
Example OID: If you want to check the system uptime of a device, you would use the OID that corresponds to this metric.
2. GETNEXT
Command: GETNEXT
Application: The GETNEXT command is used when the SNMP manager needs to retrieve the next value in a sequence of data (e.g., a list of interfaces or device statistics). It is commonly used to iterate through a collection of related objects, such as a list of interface counters on a switch or router.
Example Use:
If you need to retrieve information about all interfaces on a network device (such as their input/output counters), the GETNEXT command would help the manager walk through each interface one by one.
How it works: The SNMP manager sends a request for the next object in the MIB (Management Information Base) hierarchy. The agent responds with the next available object based on the OID.
3. SET
Command: SET
Application: The SET command is used by the SNMP manager to modify or set the value of an object on the SNMP agent. This command allows administrators to configure devices remotely, such as changing interface settings, adjusting device parameters, or enabling/disabling specific features.
Example Use:
You can use the SET command to change the configuration of a network device, such as enabling or disabling an interface or adjusting the device's settings.
How it works: The SNMP manager sends a SET request with the OID of the parameter it wants to change and the new value. The agent then updates the parameter accordingly.
Example: Changing the IP address of an SNMP-enabled device or adjusting a device’s threshold value for triggering alerts.
4. TRAPS
Command: TRAP
Application: SNMP traps are asynchronous messages sent from the SNMP agent to the SNMP manager to notify it about events or problems, such as high error rates, device reboots, or thresholds being exceeded. Unlike the other commands, which are initiated by the manager, traps are sent by the agent without a request from the manager.
Example Use:
A router may send a trap if its CPU usage exceeds a certain threshold, or if an interface goes down, to alert the SNMP manager about a potential issue.
How it works: The SNMP agent sends an unsolicited TRAP message to the SNMP manager. This message contains the OID of the object that triggered the trap, along with relevant information such as the severity of the event or the state of the device.
Example: A router sends a trap to the SNMP manager indicating that an interface has gone down or a system error has occurred.

Why Golden Signals Matter for Monitoring
Key SNMP Metrics for Network Monitoring
Network administrators use SNMP (Simple Network Management Protocol) to monitor devices across a network.
Here’s a breakdown of some commonly monitored SNMP metrics and how they support in network monitoring:
1. System Uptime (sysUpTime)
- OID: 1.3.6.1.2.1.1.3.0
- Description: This metric tracks how long the device has been up since its last reboot, offering insight into the stability of the device.
- Use in Monitoring: A short uptime can signal issues like unexpected crashes or power failures.
2. CPU Utilization (hrProcessorLoad)
- OID: 1.3.6.1.2.1.25.3.3.1.2
- Description: Measures the percentage of CPU usage. High usage can indicate that the device is overburdened or facing performance issues.
- Use in Monitoring: High CPU utilization can signal the need for optimization or a hardware upgrade, especially for devices like routers or servers.
3. Memory Utilization (memTotalFree)
- OID: 1.3.6.1.4.1.2021.4.6.0 (total memory), 1.3.6.1.4.1.2021.4.11.0 (free memory)
- Description: Tracks the total and available memory on a device, which is crucial for ensuring there’s enough memory for processes.
- Use in Monitoring: High memory usage or low free memory can affect performance, especially for memory-intensive applications.
4. Network Interface Utilization (ifInOctets, ifOutOctets)
- OID: 1.3.6.1.2.1.2.2.1.10 (incoming bytes), 1.3.6.1.2.1.2.2.1.16 (outgoing bytes)
- Description: Measures the number of bytes transmitted and received through a network interface.
- Use in Monitoring: High traffic may indicate network congestion or bandwidth limitations, requiring attention to optimize traffic flow.
5. Packet Loss (ifInDiscards, ifOutDiscards)
- OID: 1.3.6.1.2.1.2.2.1.13 (input discards), 1.3.6.1.2.1.2.2.1.19 (output discards)
- Description: Tracks the number of discarded packets due to errors, congestion, or overflow.
- Use in Monitoring: Excessive packet loss can indicate network problems, such as congestion or faulty hardware, which can degrade performance.

Docker Monitoring with Prometheus: A Step-by-Step Guide
6. Interface Errors (ifInErrors, ifOutErrors)
- OID: 1.3.6.1.2.1.2.2.1.14 (input errors), 1.3.6.1.2.1.2.2.1.20 (output errors)
- Description: Measures errors on network interfaces, such as checksum or framing errors.
- Use in Monitoring: Interface errors can highlight issues with cables, configurations, or network congestion, requiring troubleshooting to ensure optimal performance.
7. Temperature (envMonTemperature)
- OID: 1.3.6.1.4.1.9.9.13.1.3
- Description: Tracks the internal temperature of devices to avoid overheating, which could damage hardware.
- Use in Monitoring: Overheating can cause device failures or reduced performance, making temperature monitoring especially important in data centers.
8. Disk Space (hrStorageUsed, hrStorageSize)
- OID: 1.3.6.1.2.1.25.2.3.1.5 (used disk space), 1.3.6.1.2.1.25.2.3.1.3 (total disk space)
- Description: Monitors the available and used disk space on devices like servers or storage systems.
- Use in Monitoring: Running out of disk space can lead to system failures or degraded performance, so it’s essential to monitor disk usage regularly.
9. Network Throughput (ifHighSpeed)
- OID: 1.3.6.1.2.1.2.2.1.15
- Description: Indicates the maximum bandwidth capacity of a network interface.
- Use in Monitoring: Monitoring throughput helps ensure that network interfaces are not being overburdened, and traffic levels stay within manageable limits.
10. Power Supply Status (powerSupplyStatus)
- OID: 1.3.6.1.4.1.9.9.14.1.7
- Description: Provides the power status, indicating whether the device is running on AC power or backup power (such as a battery).
- Use in Monitoring: Power status monitoring ensures network devices are always operational and helps prevent unexpected outages or downtime.
SNMP Protocol Versions
There are three main versions: SNMPv1, SNMPv2c, and SNMPv3.
Each version brings its features and improvements, catering to different network environments.
1. SNMPv1 (SNMP Version 1)
- Released: 1988
- Overview: The first version of SNMP, widely used in smaller networks due to its simplicity. However, it's considered insecure by today’s standards.
Key Features:
- Message Types: GET, SET, and TRAP operations for basic communication.
- Authentication: Uses community strings (plaintext passwords), which makes it vulnerable to interception.
- Security: Limited to basic access control with no encryption.
- MIB Support: A simple MIB (Management Information Base) structure for monitoring resources.
Use Case: Best for simpler, non-sensitive environments where ease of setup and basic functionality are the priorities.
2. SNMPv2c (SNMP Version 2c)
- Released: 1993
- Overview: An improved version of SNMPv1 that adds better performance, error handling, and more efficient data collection.
Key Features:
- Message Types: Adds GETBULK and INFORM operations for better error handling and more efficient data retrieval.
- Error Handling: Enhanced with error codes for troubleshooting.
- Authentication: Still relies on community strings, maintaining the same security flaws as SNMPv1.
- Performance: Supports bulk data retrieval, making it better for larger networks.
Use Case: Suitable for networks that require better performance and error reporting but don’t need strong security, or where external security measures (like VPNs) are in place.

Observability vs. Telemetry vs. Monitoring
3. SNMPv3 (SNMP Version 3)
- Released: 1998
- Overview: The most secure and feature-rich version of SNMP. It addresses the security vulnerabilities of SNMPv1 and SNMPv2c, providing robust encryption and authentication.
Key Features:
- Security: Includes both authentication (MD5, SHA) and encryption (DES, AES), ensuring secure communication.
- Access Control: Fine-grained control over who can perform SNMP operations on a device, with user-based security.
- Message Types: Retains basic message types but adds security options.
- Privacy and Integrity: Ensures both data confidentiality and integrity.
Use Case: Best suited for security-sensitive environments (e.g., government, finance, healthcare), where data privacy and access control are paramount.
Challenges of SNMP Monitoring
While SNMP monitoring is a powerful tool, it’s not without its challenges. Some common issues include:
Overloading the Network
If polling intervals are too short or too many devices are being monitored at once, SNMP can overload your network. It’s essential to find a balance that allows for timely data collection without overwhelming your infrastructure.
Device Compatibility
Not all devices support SNMP or expose the same data. In some cases, custom MIB files may be required to monitor specific devices effectively.
Security Concerns
Older versions of SNMP (like v1 and v2c) lack strong security features, making them vulnerable to attacks. Always prioritize using SNMPv3 to mitigate these risks.
Comparison of SNMP Versions
| Feature | SNMPv1 | SNMPv2c | SNMPv3 |
|---|---|---|---|
| Security | Minimal (Community String) | Minimal (Community String) | Strong (Authentication & Encryption) |
| Performance | Basic functionality | Improved (GETBULK) | Enhanced (but more resource-intensive) |
| Error Handling | Basic | Improved | Improved with security context |
| Message Types | GET, SET, TRAP | GET, SET, TRAP, GETBULK, INFORM | GET, SET, TRAP, GETBULK, INFORM with security |
| Access Control | None | None | Fine-grained (User-based) |
| Encryption | None | None | Yes (DES, AES) |
| Use Case | Small, simple networks | Medium networks, larger setups | Large, complex, security-sensitive networks |
Choosing the Right SNMP Version
When deciding which SNMP version to implement, consider the following factors:
- Security Requirements: If you need robust security (authentication and encryption), SNMPv3 is the clear choice.
- Performance Needs: For networks that need efficient data collection, SNMPv2c is a great option with its GETBULK operation.
- Simplicity and Legacy Support: If security is not a top concern and you need a simple setup, SNMPv1 may still be useful for small, less critical networks.
Best Practices for Implementing SNMP Monitoring
Choose the Right SNMP Monitoring Tool
There are various SNMP monitoring tools available, ranging from open-source solutions like Prometheus to commercial products like SolarWinds. When selecting a tool, consider the size of your network, the complexity of your monitoring needs, and your budget. Look for tools that offer:
- Easy integration with your network infrastructure
- Real-time data visualization and alerts
- Support for SNMP versions 1, 2c, and 3
- Detailed reporting and historical data analysis
Define Key Metrics to Monitor
Not all metrics are equally important. Define what’s most relevant for your network’s health and focus on monitoring the following key metrics:
- CPU and Memory Usage: Keep track of resource usage to prevent bottlenecks.
- Network Throughput: Monitor bandwidth utilization to avoid congestion.
- Device Uptime: Check for device failures or reboots.
- Error Rates: Track packet loss, retransmissions, and other error metrics.
By focusing on these critical metrics, you can quickly identify performance issues without getting overwhelmed by excessive data.
Set Up Alerts and Thresholds
Alerts are essential for proactive network monitoring. Most SNMP monitoring tools allow you to configure thresholds for various metrics. For example, you might set up an alert to notify you if CPU usage exceeds 90%. This allows you to take action quickly before the issue impacts network performance.
Keep Your MIB Files Updated
MIB files are regularly updated by device manufacturers to include new devices or updated metrics. Ensure that your MIB files are up to date to maintain full compatibility with the devices in your network. This will help you gather the most accurate and comprehensive data.

Secure SNMP Communications
SNMPv3 offers enhanced security over previous versions by supporting encryption and authentication. If security is a concern, it’s recommended to use SNMPv3 to prevent unauthorized access and ensure data integrity.
Conclusion
SNMP monitoring is an essential tool for network management, offering a reliable way to track the performance and health of your network devices.
When implemented with the right tools and best practices, SNMP becomes a key part of your network strategy, providing valuable insights that help keep your network optimized and secure.