Application performance can make or break user experiences. Application monitoring is more than just tracking metrics; it's about ensuring reliability, proactively identifying issues, and maintaining users' trust.
This guide explores the best practices for application monitoring, helping you optimize performance while avoiding potential pitfalls.
What Is Application Monitoring?
Application monitoring involves tracking key aspects of your software's performance, availability, and health to understand its behavior and address any issues.
It’s essential to ensure that your application performs well under all conditions and provides a smooth experience for users.
Key Components of Application Monitoring
- Performance Metrics: Measure response times, transaction throughput, and resource utilization to maintain efficient operations.
- Availability Tracking: Ensure your application is always accessible, minimizing unplanned downtime.
- Error Detection: Identify and log errors or exceptions to debug effectively.
- User Experience Monitoring: Assess how users interact with your application to spot performance bottlenecks.
- Security Monitoring: Detect and mitigate vulnerabilities to keep your application secure.
The Essentials of SNMP Monitoring in Networks
Why Is Application Monitoring Important?
Monitoring applications ensure they meet performance benchmarks, improve user satisfaction, and comply with service level agreements (SLAs).
It also provides actionable insights for developers and operations teams, enabling them to make data-driven decisions.
Understanding and Mapping Application Dependencies for Better Monitoring
Modern applications rarely operate in isolation. They’re often part of a complex ecosystem of services, databases, APIs, and external integrations.
Understanding and mapping these dependencies is critical for accurate monitoring and efficient problem resolution.
Why Dependency Mapping Matters
Improved Monitoring Accuracy
Without a clear view of how components interact, it’s easy to misinterpret performance data.
For example, a database query slowing down might not be the database’s fault but a bottleneck in the application server. Dependency mapping helps pinpoint the true source of issues.
Faster Problem Resolution
When an issue arises, knowing the relationships between components accelerates root cause analysis. Instead of wading through logs and guesses, teams can follow the dependency chain to identify and resolve problems quickly.
Proactive Issue Prevention
Understanding dependencies allows you to monitor critical paths and weak links, enabling proactive fixes before they affect users.
Adapting to Change
As applications evolve, new services and integrations are introduced. Mapping dependencies ensures monitoring remains accurate and relevant despite these changes.
How to Map Application Dependencies
Create a Visual Map
Use diagrams or tools to visually represent your application’s architecture, including all services, databases, APIs, and third-party integrations. Highlight the connections and interactions between components.
Use Observability Tools
Tools like distributed tracing, log aggregation, and metric monitoring can automatically discover and map dependencies by analyzing communication patterns.
Involve All Stakeholders
Team up with teams across development, operations, and security to ensure all dependencies are identified. Different teams often have unique insights into how components interact.
Keep the Map Updated
Applications are dynamic, so your dependency map must evolve with them. Regularly review and update the map to reflect new dependencies, removed components, or architecture changes.
Monitor Dependency-Specific Metrics
Track metrics specific to each dependency, such as API response times, database query speeds, or network latency. This granularity ensures no critical dependency is overlooked.
The Basics of Network Device Monitoring Explained
Tools and Techniques for Dependency Mapping
Distributed Tracing
Tools like OpenTelemetry, Jaeger, or Zipkin help track requests across services, revealing how components interact.
Service Meshes
Platforms like Istio or Linkerd can provide insights into service-to-service communication.
Infrastructure Monitoring
Tools like Prometheus or Last9 offer dependency insights through metrics and visualizations.
Choosing the Right Metrics: The Key to Meaningful Application Monitoring
Metrics are the lifeblood of application monitoring, offering a window into how your systems are performing. However, not all metrics are created equal.
Monitoring everything indiscriminately can lead to information overload, obscure critical insights, and make troubleshooting harder.
Focusing on the right metrics ensures you’re capturing meaningful data that truly reflects your application’s performance and health.
Why Choosing the Right Metrics Matters
Avoiding Noise
Tracking too many metrics creates a flood of data, making it difficult to distinguish actionable information from irrelevant details. By focusing on key metrics, you reduce noise and improve clarity.
Aligning with Business Goals
Metrics should reflect what matters to your business and users. For example, if user experience is a priority, metrics like response time and error rates are more relevant than CPU usage alone.
Facilitating Quick Troubleshooting
When problems arise, targeted metrics make it easier to pinpoint issues. Without them, you risk spending hours sifting through data that doesn’t lead to solutions.
Optimizing Resource Use
Monitoring tools consume resources, and excessive metrics tracking can impact performance and cost. Focusing on what’s important ensures efficient resource utilization.

Why You Need Server Monitoring Tools and How to Choose
Types of Metrics to Focus On
Performance Metrics
- Response Time: Measures how quickly your application responds to user requests.
- Throughput: Tracks the volume of requests your system handles per unit of time.
- Error Rate: The percentage of failed requests or transactions, crucial for identifying user-impacting issues.
Resource Utilization Metrics
- CPU and Memory Usage: Indicates how efficiently your application uses system resources.
- Disk I/O: Helps identify bottlenecks in data read/write operations.
User Experience Metrics
- Page Load Times: Directly impacts user satisfaction and retention.
- Apdex Score: A composite metric reflecting user-perceived performance.
Reliability Metrics
- Uptime: Measures the availability of your application or service.
- MTTR (Mean Time to Recovery): Tracks how quickly you resolve issues when they occur.
Business-Centric Metrics
- Conversion Rates: For e-commerce or subscription-based platforms, this reflects how well the application supports business goals.
- Churn Rate: Tracks user retention and satisfaction.

Why Cloud Security Monitoring is Crucial for Your Business
Best Practices for Selecting Metrics
Understand Your Audience
Metrics should serve the needs of all stakeholders—developers, operations teams, and business leaders. Technical metrics might matter to engineers, while user experience and business metrics resonate with leadership.
Use the RED and USE Methods
- RED (Rate, Errors, Duration): Focuses on critical performance metrics for request-based systems.
- USE (Utilization, Saturation, Errors): Targets infrastructure health metrics, helping prevent resource bottlenecks.
Set Baselines and Benchmarks
Define what “normal” looks like for your metrics. Use industry benchmarks and historical data to identify deviations that require action.
Regularly Reevaluate Metrics
As your application evolves, so should your monitoring. Periodically review and adjust your metrics to ensure they remain relevant and aligned with your goals.
Visualize Metrics Effectively
Use dashboards to present metrics in a way that’s easy to interpret. Group related metrics and use clear labels and thresholds to highlight critical insights.
Pitfalls to Avoid
- Focusing Solely on System Metrics: While CPU and memory usage are important, they don’t always correlate with user experience. Include user-centric metrics for a holistic view.
- Overcomplicating Dashboards: A cluttered dashboard with too many metrics can overwhelm teams. Keep it clean and focused.
- Neglecting Context: Metrics without context (e.g., traffic spikes due to a marketing campaign) can lead to misinterpretation.

DNS Monitoring: Everything You Need to Know
Configuring Alerts and Notifications for Timely Interventions
Application monitoring is only as effective as its ability to prompt action. Configuring alerts and notifications ensures that stakeholders are promptly informed of performance issues or anomalies, enabling swift intervention before they escalate into larger problems.
The Role of Alerts in Application Monitoring
Proactive Issue Resolution
Alerts allow teams to identify and address potential problems before users notice them, reducing downtime and protecting user experience.
Minimized Impact
Quick notifications help mitigate the damage caused by issues such as resource bottlenecks, latency spikes, or service disruptions.
Simplified Communication
Configured alerts ensure that the right people receive timely information, preventing delays and confusion during incident response.
Best Practices for Configuring Alerts
Define What’s Critical
Not every anomaly requires immediate attention. Configure alerts for critical metrics that directly impact application performance, such as:
- High error rates
- Resource saturation (e.g., CPU or memory)
- Latency exceeding thresholds
- Service unavailability
Set Thresholds Intelligently
Establish thresholds that strike a balance between sensitivity and practicality. Overly aggressive thresholds can lead to alert fatigue, while lenient ones might miss significant issues. Use historical data to determine appropriate values.
Use Different Severity Levels
Classify alerts by severity to prioritize responses effectively. For example:
- Critical: Requires immediate action (e.g., service downtime).
- Warning: Indicates a potential issue (e.g., a resource nearing saturation).
- Informational: Non-urgent updates for tracking trends or changes.
Tailor Alerts to the Audience
Not all stakeholders need the same level of detail. Developers might need in-depth technical insights, while business leaders require high-level summaries of user impact. Configure notifications to match each audience’s needs.
Use Multiple Notification Channels
Ensure alerts reach stakeholders through their preferred channels, such as:
- Messaging platforms (e.g., Slack, Microsoft Teams)
- Incident management tools (e.g., PagerDuty, Opsgenie)
- SMS for urgent, critical alerts
Incorporate Context in Alerts
Provide actionable information in alert messages, such as:
- Affected systems or services
- Root cause hypotheses (if available)
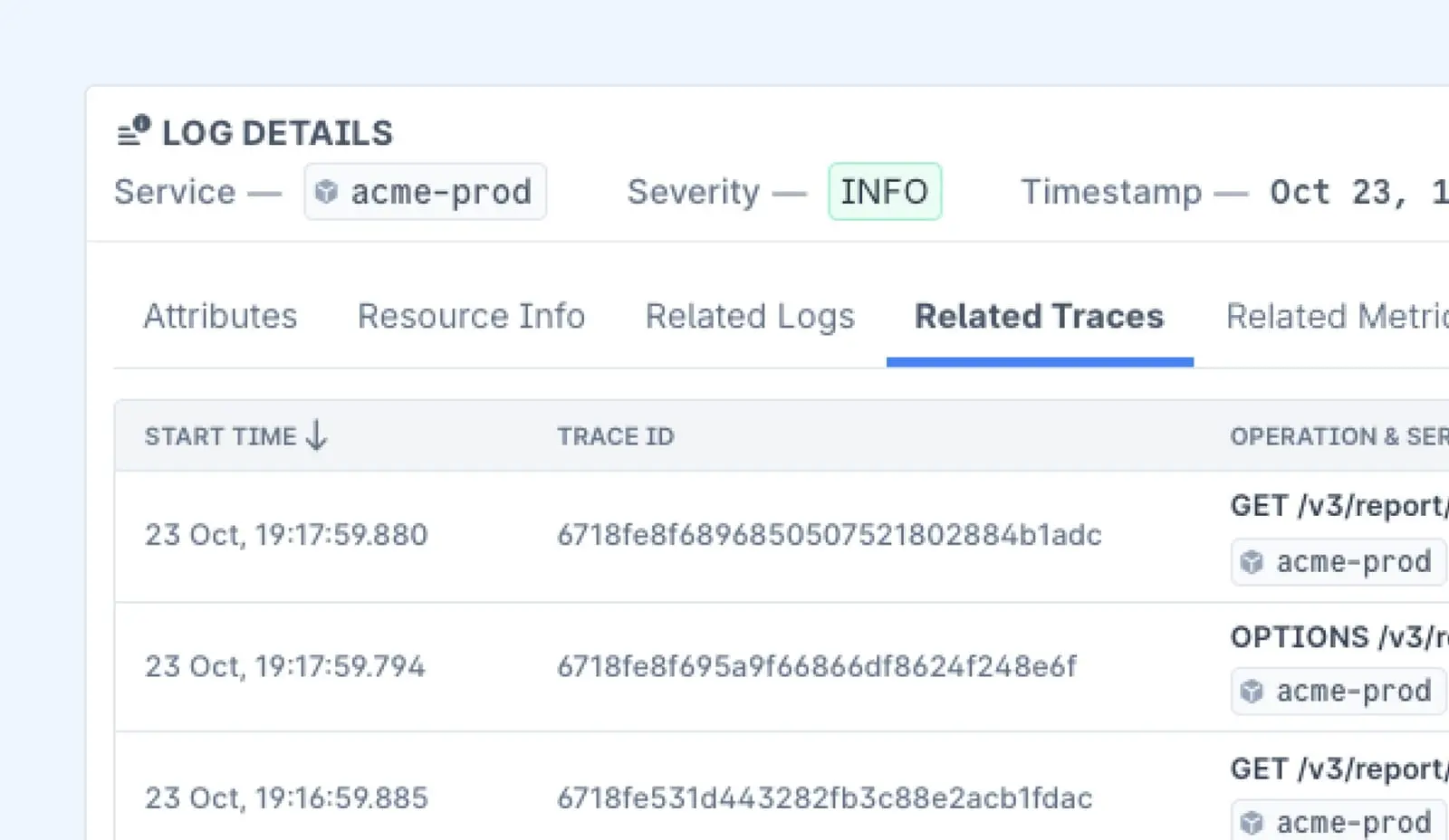
- Relevant logs, traces, or metrics for further investigation
Test Alerts Regularly
Periodically test alert configurations to ensure they’re functioning as intended and reaching the right recipients. Simulated incidents can help fine-tune settings.

API Monitoring: A Comprehensive Guide for Developers
Common Pitfalls to Avoid
- Alert Fatigue: Too many alerts, especially false positives, can desensitize teams and lead to missed critical notifications. Focus on actionable alerts.
- Generic Notifications: Alerts without sufficient context or clarity can slow down response times. Include meaningful details to guide intervention.
- Ignoring Escalation Policies: Ensure that alerts escalate appropriately if they aren’t acknowledged or resolved within a set timeframe.
Tools to Enhance Alerting Practices
- Prometheus Alertmanager: For defining alerting rules and managing notifications.
- Grafana: Integrates with various monitoring tools to send alerts based on visualization thresholds.
- Opsgenie/PagerDuty: Specialized tools for incident management and notification escalation.
- Slack/Teams Integrations: Connect monitoring tools with communication platforms for real-time updates.
Integrating Security and Compliance into Application Monitoring
Monitoring isn’t just about performance and uptime—it’s also about safeguarding data and adhering to regulatory standards.
Integrating security and compliance considerations into the application monitoring process ensures your applications remain not only reliable but also secure and legally compliant.
Why Security and Compliance Matter in Monitoring
Protecting Sensitive Data
Applications often handle sensitive user data, from personal information to financial records.
Monitoring without considering security could expose this data to breaches or unauthorized access. Integrating security practices helps detect anomalies that might indicate potential vulnerabilities or attacks.
Meeting Regulatory Requirements
Regulations like GDPR, HIPAA, and PCI-DSS mandate strict controls on data handling, storage, and processing.
Application monitoring must align with these requirements to avoid penalties, maintain customer trust, and ensure smooth operations.
Building User Trust
Security incidents can damage reputation and erode user confidence. A monitoring process that actively tracks security metrics demonstrates your commitment to protecting user data and enhancing trust.
Best Practices for Integrating Security and Compliance
Monitor for Security Threats
Implement monitoring tools that can detect and flag potential security incidents, such as unauthorized access attempts, unusual traffic patterns, or DDoS attacks.
Use advanced techniques like anomaly detection powered by machine learning to identify threats in real-time.
Enforce Access Controls
Ensure that monitoring dashboards and logs are accessible only to authorized personnel. Role-based access control (RBAC) minimizes the risk of insider threats or accidental data exposure.
Track Compliance Metrics
Include compliance-specific metrics in your monitoring strategy, such as encryption status, data retention periods, or audit trail completeness.
Regularly review logs and reports to confirm adherence to regulatory requirements.

Top 5 Open Source SIEM Tools for Security Monitoring
Automate Security Alerts
Configure alerts for security-related events, such as failed login attempts or unauthorized configuration changes. Automating responses, like blocking IPs after multiple failed login attempts, can prevent threats from escalating.
Maintain Audit Trails
Comprehensive logging is essential for both security and compliance. Logs should capture all critical events, including user actions, system changes, and access attempts. Store these logs securely and ensure they’re tamper-proof to meet regulatory standards.
Collaborate with Security Teams
Application monitoring isn’t a siloed activity. Partner with security experts to align monitoring practices with broader security and compliance strategies.
Stay Up-to-Date with Regulations
Regulations evolve, and so should your monitoring practices. Regularly review changes in compliance requirements and update your monitoring tools and processes accordingly.
Combining Monitoring and Governance
A robust monitoring system doesn’t just measure performance; it acts as a guardian of your application’s integrity and security. By integrating security and compliance into monitoring:
- You gain real-time visibility into potential vulnerabilities and non-compliance issues.
- You can respond swiftly to security incidents, minimizing damage.
- You demonstrate accountability and commitment to protecting both user data and your organization’s reputation.
How Collaboration and Ownership Boost Application Monitoring
Effective application monitoring is not just about tools and processes—it’s also about people. Encouraging contribution and a sense of ownership among team members play a critical role in ensuring that monitoring is proactive and problem-solving is efficient.
Why Collaboration Matters
Modern applications are complex, often involving multiple teams like development, operations, product management, and even customer support. Silos can create gaps in understanding and response time, leading to delayed resolutions and increased frustration.
Working together bridges these gaps by ensuring:
- Shared Context: Everyone understands the big picture, including how their part of the system impacts the whole.
- Faster Problem-Solving: Issues can be diagnosed and resolved quicker when multiple perspectives come together.
- Better Decision-Making: Input from diverse teams ensures that monitoring strategies are robust and aligned with business goals.

Proactive Monitoring: What It Is, Why It Matters, & Use Cases
Encouraging Ownership Among Team Members
Ownership means every team member feels accountable for the application’s performance and reliability. This mindset transforms monitoring from a reactive task to a proactive commitment. When team members take ownership, they are more likely to:
- Anticipate Issues: Actively look for potential weak points in the system before they cause problems.
- Respond Quickly: Take initiative in resolving incidents without waiting for instructions.
- Optimize Continuously: Suggest and implement improvements to monitoring practices and system performance.
How to Encourage Collaboration and Ownership
Encourage Cross-Team Communication
Hold regular meetings where teams can discuss challenges, share insights, and align on monitoring strategies.
Use platforms to make data and insights accessible to everyone.
Define Clear Roles and Responsibilities
Make it clear who owns what aspect of the monitoring process. When accountability is defined, teams work more effectively and avoid duplication of effort.
Promote a Blameless Culture
In the event of incidents, focus on learning and improving rather than assigning blame. This builds trust and encourages team members to take ownership without fear of repercussions.
Provide Training and Resources
Equip teams with the knowledge and tools they need to understand the monitoring process. When people feel confident in their abilities, they’re more likely to take initiative.
Celebrate Successes
Acknowledge and reward contributions to monitoring and problem-solving efforts. Recognizing achievements motivates teams to stay engaged and proactive.

Why Golden Signals Matter for Monitoring
Setting Performance Goals for Effective Application Monitoring
Application monitoring without defined goals is like navigating without a map—you might end up somewhere, but it’s unlikely to be where you intended. Establishing clear performance objectives ensures that monitoring efforts are purposeful, targeted, and aligned with your business needs and user expectations.
Why Performance Objectives Are Essential
Focus on What Matters
Applications generate vast amounts of data, but not all metrics are equally important. Clear objectives help you focus on the most relevant performance indicators, reducing noise and enabling quicker insights.
Align with Business Goals
Monitoring objectives should directly support broader business priorities, such as improving customer satisfaction, meeting SLAs, or reducing operational costs. This alignment ensures monitoring contributes value beyond just technical insights.
Enhance User Experience
Objectives that prioritize user-centric metrics like page load times, transaction success rates, or error frequencies ensure that your monitoring strategy actively enhances the end-user experience.
Simplify Troubleshooting
When teams know what metrics matter and why, they can quickly identify and address issues that impact performance. This minimizes downtime and ensures smoother operations.
How to Define Effective Performance Objectives
Understand Business and User Needs
Engage with stakeholders across teams to identify what matters most to the business and its users. For example, an e-commerce site might prioritize checkout speed and uptime, while a SaaS platform may focus on API response times and reliability.
Set SMART Objectives
Ensure your objectives are Specific, Measurable, Achievable, Relevant, and Time-bound. For instance:
- Reduce average page load time to under 2 seconds within 3 months.
- Maintain 99.9% API uptime over the next quarter.
Prioritize Key Metrics
Identify a handful of metrics that best represent performance. Common examples include:
- Response Times: How long it takes for a system to respond to user requests.
- Error Rates: The frequency of errors or failed transactions.
- Throughput: The number of transactions or requests handled per second.
- Resource Utilization: CPU, memory, or bandwidth usage.

OTEL Collector Monitoring: Best Practices & Guide
Incorporate Benchmarks and SLAs
Use industry benchmarks and internal service level agreements as a baseline for setting objectives. This provides a clear standard for measuring success.
Balance Ambition and Realism
Set challenging yet achievable objectives. Overly ambitious goals can demoralize teams, while objectives that are too easy may fail to drive meaningful improvements.
The Role of Objectives in Monitoring
Proactive Issue Detection
Clear objectives help you monitor against expected baselines, enabling you to detect deviations and address them before they escalate.
Performance Optimization
Objectives guide teams in identifying areas for improvement, such as bottlenecks or inefficiencies.
Consistent Reporting
When objectives are well-defined, reporting becomes more structured and meaningful, enabling stakeholders to track progress effectively.
Best Practices for Application Monitoring
1. Define Clear Goals
Before implementing monitoring tools or strategies, outline your objectives. Are you focusing on uptime, optimizing performance, or improving customer experience? Knowing your goals will shape your monitoring approach and metrics.
2. Choose the Right Tools
Different applications require different monitoring solutions. Evaluate tools based on your architecture (e.g., microservices, monolithic, or serverless) and needs. Tools like Prometheus, Grafana, or OpenTelemetry can provide comprehensive monitoring capabilities.
3. Monitor the Entire Stack
Ensure you’re not just monitoring the application layer but also the infrastructure it relies on. Include databases, APIs, servers, and network components in your monitoring strategy to gain a holistic view.
4. Set Up Alerts Wisely
Configure alerts that are actionable and relevant. Avoid over-alerting, which can lead to alert fatigue, making teams less responsive to critical issues. Focus on thresholds and conditions that indicate actual problems.
5. Regularly Review and Update Metrics
Your application evolves, and so should your monitoring strategy. Periodically assess the relevance of the metrics you’re tracking and update them based on new features or performance goals.
6. Implement Automation
Use automation to simplify responses to common issues. Automated remediation, such as restarting a failed service or scaling resources, can save time and reduce manual intervention.
7. Focus on User Experience
Beyond backend metrics, pay attention to how users experience your application. Tools that track frontend performance, page load times, and user interactions provide valuable insights into customer satisfaction.
8. Log Everything, But Be Smart About It
Comprehensive logging is essential for debugging, but excessive logs can increase storage costs and make analysis cumbersome. Implement logging best practices, such as log rotation and structured logging.
9. Contribute Across Teams
Application monitoring isn’t just the responsibility of operations teams. Encourage collaboration between developers, operations, and product teams to align monitoring goals with business objectives.
10. Continuously Improve
Treat monitoring as an iterative process. Analyze trends, learn from incidents, and refine your monitoring approach to ensure it keeps pace with your application’s growth and complexity.
Wrapping Up
Effective application monitoring goes beyond being a technical requirement—it’s a foundational practice for maintaining reliability and enhancing user trust.
Implementing these best practices ensures that your application remains performant, secure, and user-friendly.
Stay proactive, adapt to changes, and make monitoring an integral part of your software lifecycle.













