Keeping your web applications safe from unwanted visitors has become a non-negotiable part of running anything online. From data breaches to app slowdowns or full-on crashes, the risks are real—and they’re growing. That’s why having a Web Application Firewall (WAF) is no longer just an option; it’s a smart step forward.
AWS WAF, or Amazon Web Services Web Application Firewall, is a tool designed to help you filter out the bad traffic while keeping the good stuff flowing. How does it do that? And why does it matter for businesses trying to stay secure and reliable?
Let’s understand what AWS WAF brings to the table in a way that makes sense for your needs.
What is AWS WAF?
AWS WAF is a cloud-native web application firewall that helps protect web applications from common threats and vulnerabilities.
It works by filtering, monitoring, and blocking malicious HTTP and HTTPS traffic before it reaches your application. AWS WAF allows you to define custom security rules to block or allow requests based on various factors like IP addresses, HTTP headers, URI paths, and more.
Unlike traditional firewalls that focus on network traffic, AWS WAF is tailored for web application security. It’s especially designed to protect against threats like SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities.
Key Benefits of AWS WAF for Your Web Applications
AWS WAF offers several key benefits that make it a top choice for web application security, especially for businesses running on AWS infrastructure:
1. Scalability and Flexibility
Since AWS WAF is built into AWS services like Amazon CloudFront, AWS Application Load Balancer (ALB), and Amazon API Gateway, it can scale effortlessly with your application.
Whether you’re handling a few requests per minute or millions, AWS WAF adjusts to meet your needs without requiring manual intervention. The flexibility allows you to tailor security policies to match your exact business requirements.
2. Customizable Rule Sets
One of the standout features of AWS WAF is its customization capabilities. You can create custom security rules based on the specifics of your application.
Whether it's blocking traffic from certain geographic locations, restricting access to specific IPs, or preventing certain query strings in the URL, AWS WAF lets you fine-tune security policies to match your needs.
3. Cost-Effectiveness
AWS WAF is a pay-as-you-go service, meaning you only pay for what you use. You’re charged based on the number of rules you create and the number of requests your application processes.
This makes it an economical choice, especially for businesses that need scalable security without a huge upfront investment.
4. Real-Time Visibility and Monitoring
AWS WAF integrates easily with Amazon CloudWatch, enabling you to monitor your web traffic in real-time.
You can track blocked requests, see attack patterns, and adjust your security policies accordingly. This visibility ensures that you're always aware of potential threats and can act quickly to mitigate them.
5. Managed Rules
AWS offers pre-configured, managed rule sets that automatically protect your application from common threats.
These rules are continuously updated to address emerging security risks, ensuring that your web application is always protected against the latest vulnerabilities without manual intervention.
This feature can save significant time and effort for security teams.
AWS WAF Features You Should Know About
Now that we’ve covered the benefits, let’s take a closer look at the core features that make AWS WAF a go-to solution for cloud security.
1. IP Set Control
With AWS WAF, you can create IP sets to control traffic based on IP addresses. You can whitelist trusted IP addresses or blacklist suspicious ones, ensuring that only legitimate traffic reaches your application.
2. Geo-Blocking
Geo-blocking is another powerful feature of AWS WAF that allows you to block or allow traffic from specific countries or regions. If your web application targets specific geographies or you’re facing attacks originating from a particular region, geo-blocking can be an effective way to reduce risk.
3. Rate Limiting
AWS WAF can be configured to limit the rate of requests from a particular IP address. This helps mitigate DDoS (Distributed Denial of Service) attacks and protects your application from traffic surges that could overload your resources.
4. SQL Injection and XSS Protection
AWS WAF is equipped with pre-configured rules that automatically detect and block SQL injection attempts and Cross-Site Scripting (XSS) attacks. These are two of the most common and dangerous web application vulnerabilities. With AWS WAF, you can ensure that your applications remain secure against these attacks.
5. Logging and Metrics
With AWS WAF, you get detailed logs of all web traffic. This information can be invaluable for troubleshooting and optimizing your security configurations. By analyzing these logs, you can uncover attack patterns and adjust your rules accordingly. The integration with Amazon CloudWatch also allows you to generate detailed metrics, which helps you stay on top of potential threats.
How AWS WAF Works
AWS WAF works by inspecting incoming web traffic to your application before it reaches your server.
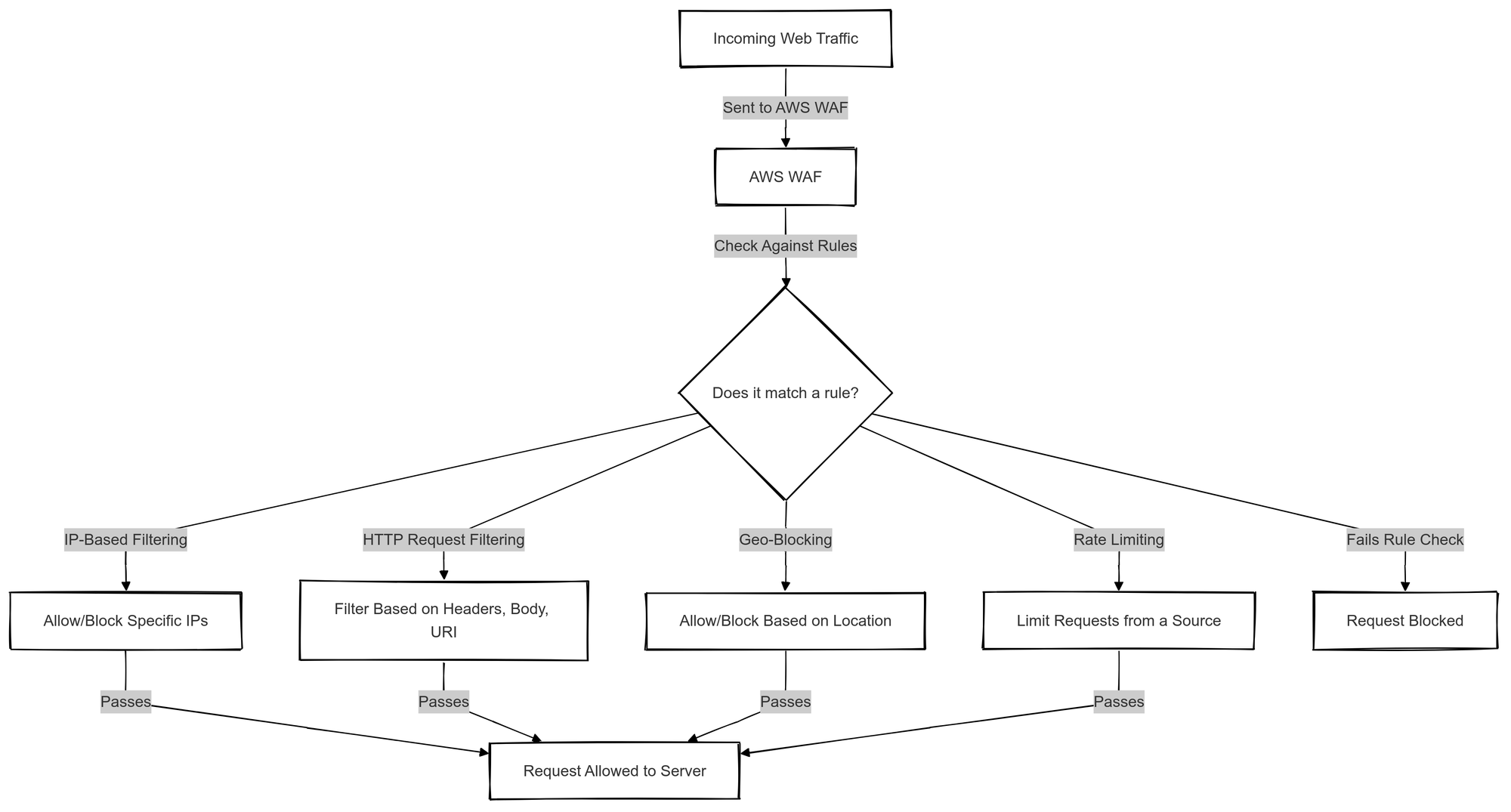
It uses rules that you define to determine whether to allow or block specific requests based on certain criteria. These rules can be tailored to your application’s needs and may include:
- IP-based filtering: Allowing or blocking specific IPs or IP ranges.
- HTTP request characteristics: Filtering traffic based on HTTP headers, body, or URIs.
- Geography: Restricting access based on the geographic location of the request.
- Rate-based filtering: Limiting the number of requests from a specific source in a given period.
How to Set Up AWS WAF in 8 Easy Steps
If you're new to AWS Web Application Firewall (AWS WAF), it can seem like a lot to take in at first.
Below is a step-by-step guide to help you get up and running with AWS WAF.
Step 1: Set Up an AWS Account
Before you can use AWS WAF, you’ll need an AWS account. If you don’t already have one, follow these steps to set it up:
- Go to the AWS Sign-Up page.
- Create an account by entering your email, password, and other basic details.
- Once your account is created, sign in to the AWS Management Console.
Step 2: Choose the Right AWS Service to Use with AWS WAF
AWS WAF is integrated with several AWS services. You'll need to choose where to apply your firewall rules. The most common services include:
- Amazon CloudFront: A content delivery network (CDN) service that delivers your content globally with low latency.
- AWS Application Load Balancer (ALB): A service that automatically distributes incoming application traffic across multiple targets, such as EC2 instances.
- Amazon API Gateway: A service for creating, deploying, and managing APIs.
Choose one of these services to associate with your AWS WAF. For example, if you're using CloudFront to serve your application globally, you'd apply WAF rules to your CloudFront distribution.
Step 3: Create Your First Web ACL
A Web ACL (Access Control List) is a collection of rules that AWS WAF uses to monitor and control incoming traffic to your application. Here’s how to create one:
- Navigate to AWS WAF Console: In the AWS Management Console, search for "WAF" in the search bar and select "AWS WAF & Shield" from the dropdown.
- Create a Web ACL:
- Click Create web ACL.
- Choose the region where your resource (CloudFront, ALB, or API Gateway) is located. For CloudFront, select “Global” because CloudFront is a global service.
- Name your Web ACL (e.g., "MyAppWAF") and provide a description.
- Select Default action for your Web ACL. This is the action taken when a request doesn't match any rule (you can choose to allow or block it).
- Select your AWS resource to associate with this Web ACL (CloudFront, ALB, etc.).
- Click Create.
Step 4: Add Rules to Your Web ACL
Now that your Web ACL is set up, it’s time to define the rules to filter traffic. AWS WAF lets you choose from predefined managed rule groups or create custom rules based on your application’s needs.
Managed Rules (Pre-Configured Rules)
AWS offers pre-configured rule sets for common attack patterns, like SQL injection and XSS. These rules are a great starting point and automatically update as new threats emerge.
- Go to the Rules section of your Web ACL.
- Click Add rules.
- Select Add managed rule groups and choose from AWS Managed Rules or third-party managed rules (like from AWS Marketplace).
- Apply the selected rules and adjust their priorities.
Custom Rules
If you want more control, you can create custom rules:
- Click Add rules and select Create rule.
- Choose a rule type (e.g., IP sets, rate-based rules, geo-blocking).
- Define conditions, such as blocking specific IP addresses, limiting request rates, or filtering by URI paths.
- Set an action (allow or block) for the rule.
Step 5: Test Your Rules
Once you've configured your Web ACL and added rules, it’s essential to test everything. AWS WAF provides a Logging and Metrics feature to help you monitor traffic and verify that your rules are working as expected.
- Enable logging by integrating AWS WAF with Amazon CloudWatch Logs.
- Use CloudWatch Metrics to visualize blocked or allowed requests.
- Test your website or application by sending requests that match your rules and check the logs to ensure the correct action is taken.
Step 6: Fine-Tune Your Configuration
As your application grows or changes, your security needs may evolve. It’s important to regularly revisit your AWS WAF configuration and adjust your rules accordingly.
- Update Managed Rules: AWS automatically updates its managed rules, but you should check for new threats or updates periodically.
- Adjust Custom Rules: Refine your custom rules based on new attack vectors or changes in your app's traffic patterns.
- Monitor Traffic: Use CloudWatch to identify false positives (requests that were blocked but shouldn’t have been) and tweak your rules to minimize disruption.
Step 7: Automate with AWS Lambda
For more advanced users, AWS Lambda can help automate your WAF management.
You can set up Lambda functions to trigger when specific events happen in AWS WAF, such as automatically blocking a malicious IP address after a certain threshold of requests.
Here's how to integrate Lambda with AWS WAF:
- Create an AWS Lambda function that will be triggered by a WAF event (such as a blocked request).
- Set up the event source in the AWS WAF console under Web ACL settings.
- Define the Lambda function's logic to respond to incoming requests, such as blocking IPs or sending alerts.
Step 8: Regularly Review Your Security
Cloud security isn’t a one-time setup. To ensure your application remains protected, you’ll need to conduct regular reviews:
- Audit Logs: Frequently review WAF logs in CloudWatch to identify unusual traffic patterns.
- Test and Update Rules: Regularly update your rules as new threats emerge or your application evolves.
- Monitor Performance: Check the performance impact of WAF on your app. If you notice latency or blocked legitimate traffic, fine-tune your rules or add exceptions.
Best Practices for Configuring AWS WAF
To maximize the effectiveness of AWS WAF, consider the following best practices:
1. Layered Security
While AWS WAF is an essential tool in your security arsenal, it should not be your only line of defense.
Incorporate other AWS security services like AWS Shield for DDoS protection and AWS Identity and Access Management (IAM) for granular access control to build a comprehensive security strategy.
2. Regularly Review and Update Rules
Security threats evolve constantly, so it’s important to regularly review and update your AWS WAF rules.
AWS offers managed rules that are continuously updated to address new threats, but you should also keep an eye on your own custom rules to ensure they remain relevant and effective.
3. Monitor Logs and Metrics
Use AWS CloudWatch to keep an eye on your WAF logs and metrics. This allows you to spot suspicious activity early and make adjustments to your rules as needed.
Regular monitoring can also help you optimize performance by reducing unnecessary rules.
4. Automate with Lambda
You can automate your WAF management using AWS Lambda, which allows you to trigger functions based on changes in your WAF metrics or logs.
For example, you could automatically block an IP if it exceeds a certain request threshold.
AWS WAF vs Competitors: A Clear Comparison
When it comes to cloud-based Web Application Firewalls (WAF), AWS WAF faces competition from several big names, including Cloudflare, Akamai Kona Site Defender, and Microsoft Azure WAF.
Let's understand their differences in detail.
AWS WAF vs Cloudflare
Cloudflare is widely recognized for its powerful CDN and DDoS protection, providing an easy-to-use WAF that integrates well with its broader security features.
However, AWS WAF has a strong edge when it comes to deep integration with other AWS services, making it a natural choice for businesses already within the AWS ecosystem.
Key Differences:
- Customizability: AWS WAF allows businesses to create highly customizable rules tailored to their specific needs, which gives more flexibility compared to Cloudflare’s offerings.
- Advanced Security: AWS WAF offers better control over advanced security configurations with greater flexibility in traffic filtering.
AWS WAF vs Akamai Kona Site Defender
Akamai Kona Site Defender is a premium solution aimed at large-scale enterprise applications, offering strong security and performance for complex use cases.
However, this comes at a higher cost, which might not be feasible for smaller businesses or those with budget constraints.
Key Differences:
- Cost-Effectiveness: AWS WAF’s pay-as-you-go pricing structure makes it much more affordable compared to Akamai, especially for businesses with varying traffic loads.
- Flexibility in Pricing: Unlike Akamai’s fixed pricing tiers, AWS WAF’s scalable pricing means you only pay for what you use, which is ideal for businesses looking to manage costs efficiently.
AWS WAF vs Microsoft Azure WAF
Microsoft Azure WAF is a solid choice for businesses that are already using Azure’s cloud infrastructure. It offers strong integration with Azure’s suite of services, centralized management, and a range of customizable security features.
However, Azure WAF is generally best suited for companies heavily invested in the Microsoft ecosystem.
Key Differences:
- Customizability: AWS WAF excels in providing a higher level of customizability, such as tailored rules and advanced integrations with AWS Lambda.
- Advanced Features: With managed rule sets and real-time traffic monitoring, AWS WAF offers more tools to combat specific threats like SQL injections and cross-site scripting.
Why Choose AWS WAF?
AWS WAF offers several unique features that make it an appealing choice for businesses already on the AWS platform:
- Deep Integration with AWS Services: AWS WAF works easily with other AWS services like Amazon CloudFront and AWS Shield, simplifying security management.
- Customizability: The ability to craft specific rules based on your business’s needs (e.g., IP addresses, HTTP headers, URI strings) gives you more control over traffic filtering.
- Cost-Effectiveness: AWS WAF’s pay-as-you-go pricing means you only pay for the resources you use, making it an affordable option for both small businesses and larger enterprises.
- Managed Rule Sets and Real-Time Monitoring: Access to pre-configured managed rule sets helps block common web application attacks like SQL injection and XSS. In addition, AWS WAF provides real-time traffic monitoring and detailed logs to spot and mitigate threats faster.
Conclusion
AWS WAF is a powerful and flexible solution for protecting your web applications from a range of security threats.
With its customizable rule sets, real-time monitoring, and easily integration with other AWS services, AWS WAF is designed to scale your business and provide strong, reliable protection.
FAQs
What is AWS WAF?
AWS WAF (Web Application Firewall) is a cloud-native security service that protects your web applications from common threats like SQL injection, cross-site scripting (XSS), and DDoS attacks. It allows you to create custom security rules to filter and monitor HTTP/HTTPS requests based on specific criteria such as IP addresses, URI paths, and headers.
How does AWS WAF work?
AWS WAF works by examining incoming web traffic and applying the rules you define to either allow or block certain requests. You can set rules based on various factors like IP addresses, HTTP headers, or query strings, and the WAF will take action based on the conditions you’ve specified. This helps ensure that only legitimate traffic reaches your application.
What is a Web ACL in AWS WAF?
A Web ACL (Access Control List) is a set of rules you apply to your AWS resources, such as Amazon CloudFront, ALB, or API Gateway. It acts as a filter, inspecting incoming traffic and deciding whether to allow or block it based on the rules you’ve set. You can associate multiple Web ACLs with different resources.
What are AWS WAF-managed rule groups?
Managed rule groups are pre-configured, continuously updated sets of rules provided by AWS or third-party vendors. These rules are designed to protect against common threats, such as SQL injection or cross-site scripting. You can enable managed rule groups to automatically guard your applications from the latest vulnerabilities without needing to manually configure each rule.
How can I create custom rules in AWS WAF?
To create custom rules, you simply need to define the conditions you want to match—such as specific IP addresses, HTTP request characteristics, or geographic locations. You can set actions like blocking or allowing traffic based on these conditions. Custom rules are useful when you want more granular control over your web application’s security.
How does AWS WAF handle DDoS attacks?
AWS WAF helps protect against smaller-scale DDoS attacks by blocking malicious requests that exceed rate limits or come from suspicious IP addresses. For larger-scale DDoS attacks, AWS Shield provides more comprehensive protection, which works in conjunction with AWS WAF for a multi-layered defense.
Can AWS WAF be used with Amazon CloudFront?
Yes, AWS WAF is often used with Amazon CloudFront, AWS's content delivery network (CDN). You can configure AWS WAF to protect CloudFront distributions, ensuring that malicious traffic is blocked before it reaches your content, and reducing the risk of attacks like DDoS and SQL injection.
How much does AWS WAF cost?
AWS WAF operates on a pay-as-you-go pricing model. You are charged based on the number of rules you configure and the amount of web requests your application processes. There are no upfront costs, and you can scale your usage up or down based on demand, which makes AWS WAF cost-effective for businesses of all sizes.
Can I use AWS WAF with multiple AWS resources?
Yes, AWS WAF can be used with multiple AWS resources. You can apply the same Web ACL to different AWS services, such as CloudFront, Application Load Balancer (ALB), and API Gateway. This allows you to create a unified security layer across your application infrastructure.
What logging and monitoring capabilities does AWS WAF provide?
AWS WAF integrates with Amazon CloudWatch to provide real-time logging and monitoring. You can view detailed logs of web requests that are allowed or blocked based on your rules. CloudWatch Metrics also allows you to track the number of requests, helping you identify patterns or potential attacks.
Is AWS WAF difficult to configure?
AWS WAF is designed to be flexible and relatively simple to configure. You can start with pre-configured managed rule groups or create custom rules based on your specific needs. The AWS Management Console provides an easy-to-use interface for setting up and managing your Web ACLs and rules, making it accessible even for those new to AWS services.
What is the difference between AWS WAF and AWS Shield?
AWS WAF and AWS Shield serve different purposes. AWS WAF focuses on filtering and blocking malicious web traffic based on custom and managed rules, while AWS Shield is a managed DDoS protection service designed to safeguard against larger-scale attacks. AWS Shield and AWS WAF work together to provide a layered defense for your web applications.
Can I automate AWS WAF rule updates?
Yes, you can automate rule updates in AWS WAF using AWS Lambda functions. You can set up Lambda to trigger actions, such as blocking an IP address after a certain number of failed requests, based on events from AWS WAF logs or metrics. This helps simplify security management and response times.
How do I test AWS WAF rules before applying them to production?
You can test AWS WAF rules by first enabling Logging and Metrics in the AWS WAF console. This lets you monitor and analyze how your rules are affecting incoming traffic without immediately blocking requests. You can make adjustments as needed and ensure the rules don't interfere with legitimate traffic before fully applying them to production.
Can AWS WAF protect against bot traffic?
AWS WAF can help mitigate bot traffic by filtering out suspicious requests based on characteristics such as the rate of requests, IP addresses, and geographical location. Additionally, AWS WAF can be used in combination with services like AWS Bot Control for more comprehensive bot management.
Can AWS WAF block specific HTTP methods?
Yes, AWS WAF allows you to block or allow specific HTTP methods (such as GET, POST, PUT, DELETE) based on your security needs. You can configure rules to block certain methods if they’re not needed by your application or if they are often associated with attacks.
What are the security best practices when using AWS WAF?
Some best practices for AWS WAF include:
- Regularly review and update your rules to protect against emerging threats.
- Use AWS Managed Rules to automatically safeguard against common vulnerabilities.
- Enable logging and monitoring through CloudWatch to track blocked and allowed traffic.
- Implement rate-based rules to protect against DDoS attacks.
- Use multiple layers of security, combining AWS WAF with other AWS services like AWS Shield and IAM.



