As organizations expand their AWS footprint, maintaining visibility and control over configurations can be challenging. Misconfigurations, unnoticed vulnerabilities, and compliance gaps can create serious security risks.
AWS Cloud Security Posture Management (CSPM) helps teams navigate these challenges by automating security checks, ensuring compliance, and providing continuous monitoring. Here’s what you need to know about AWS CSPM and why it’s essential for securing your cloud environment.
What is AWS CSPM?
AWS Cloud Security Posture Management (CSPM) is a critical aspect of securing cloud environments, ensuring compliance, and mitigating risks. As organizations increasingly rely on AWS for their cloud workloads, the need for robust security posture management has never been greater.
CSPM refers to tools and best practices designed to identify misconfigurations, enforce security policies, and provide continuous monitoring for compliance. AWS CSPM solutions help organizations proactively detect vulnerabilities and prevent security breaches before they occur.
Why AWS CSPM is Essential
AWS provides a highly scalable and flexible cloud environment, but security is a shared responsibility. While AWS secures the infrastructure, customers must protect their workloads, applications, and configurations.
Here’s why AWS CSPM is crucial:
- Misconfiguration Detection: Many cloud breaches occur due to misconfigurations, such as overly permissive IAM policies or exposed S3 buckets.
- Compliance Assurance: Organizations operating in regulated industries must comply with standards like GDPR, HIPAA, and SOC 2. CSPM ensures configurations align with these frameworks.
- Continuous Monitoring: Unlike periodic security assessments, CSPM offers real-time visibility into security risks.
- Automated Remediation: Many CSPM tools provide automated workflows to fix security misconfigurations instantly.
Key Features of AWS CSPM
A robust AWS CSPM solution should offer the following features:
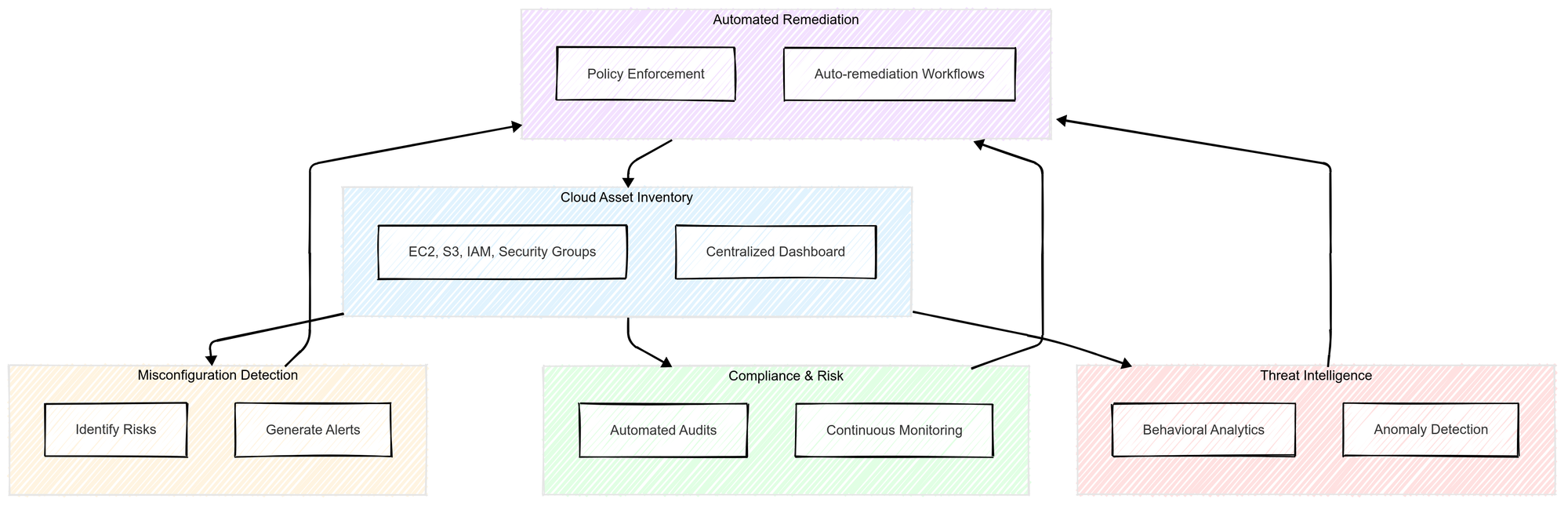
1. Cloud Asset Inventory
- Visibility into all AWS resources, including EC2 instances, S3 buckets, IAM policies, and security groups.
- Centralized dashboard for managing cloud security posture.
2. Misconfiguration Detection & Alerting
- Identifies risks like publicly accessible S3 buckets, unencrypted databases, and open security groups.
- Generates real-time alerts and recommendations for remediation.
3. Compliance & Risk Assessment
- Automated audits against compliance standards (NIST, CIS, PCI-DSS, ISO 27001).
- Continuous compliance monitoring with detailed reporting.
4. Threat Intelligence & Anomaly Detection
- Identifies suspicious activities using behavioral analytics.
- Detects unauthorized access attempts, privilege escalations, and unusual data transfers.
5. Automated Remediation
- Policy enforcement mechanisms to correct misconfigurations automatically.
- Integration with AWS Lambda and security orchestration platforms for auto-remediation workflows.
Top AWS CSPM Tools in 2025
AWS Cloud Security Posture Management (CSPM) tools help organizations achieve these goals by continuously assessing their cloud security posture.
Here’s a breakdown of the top AWS CSPM tools in 2025 and how they can help protect your cloud environment.
AWS Security Hub – Native AWS Security and Compliance
For organizations deeply integrated into AWS, AWS Security Hub provides a native solution for monitoring security posture across accounts and services. It aggregates findings from multiple AWS security tools and performs automated compliance checks.
Key features:
- Centralized security dashboard for AWS services
- Automated compliance checks (CIS, PCI DSS, NIST, etc.)
- Easy integration with AWS-native security tools like GuardDuty and Inspector
Best suited for teams looking for AWS-native security insights without third-party complexity.
Palo Alto Prisma Cloud – Multi-Cloud Security and Compliance
Prisma Cloud by Palo Alto Networks offers an advanced security solution for organizations managing workloads across AWS, Azure, and GCP. It continuously scans cloud configurations, permissions, and workloads to identify risks and enforce security best practices.
Key features:
- Security visibility across multi-cloud environments
- Misconfiguration detection and automated remediation
- Cloud workload and container security
Ideal for businesses operating in a multi-cloud environment that need comprehensive CSPM and workload protection.
Check Point CloudGuard – Automated Security and Threat Prevention
CloudGuard provides continuous security posture assessments and automatic remediation to protect AWS workloads. It also integrates threat intelligence to prevent attacks before they happen.
Key features:
- Continuous misconfiguration and security risk detection
- Automated remediation to reduce manual security tasks
- Advanced threat intelligence and attack prevention
A strong choice for organizations looking for automated CSPM with real-time threat prevention.
Lacework – AI-Driven Security and Compliance
Unlike traditional CSPM tools, Lacework uses machine learning to detect misconfigurations, security threats, and compliance violations. Instead of relying only on predefined rules, it learns your AWS environment’s behavior and flags anomalies.
Key features:
- AI-powered anomaly detection for security risks
- Automated compliance tracking and reporting
- Reduces alert fatigue by prioritizing real risks
Perfect for teams wanting an AI-driven approach to cloud security with less manual effort.
Trend Micro Cloud One – Security and Compliance at Scale
Cloud One by Trend Micro is built for large-scale AWS deployments, offering deep visibility into security misconfigurations while ensuring compliance with global regulations like GDPR, HIPAA, and SOC 2.
Key features:
- Security and compliance automation for AWS workloads
- Runtime protection for applications and services
- Continuous misconfiguration monitoring
Best for businesses that prioritize compliance and large-scale cloud security.
Which AWS CSPM Tool is Right for You?
Choosing the right CSPM tool depends on your security needs:
- If you prefer AWS-native tools, go with AWS Security Hub.
- If you need multi-cloud security, Prisma Cloud is a strong contender.
- If automated remediation and threat prevention matter most, consider CloudGuard.
- If you want an AI-driven security approach, Lacework stands out.
- If compliance is your top concern, Trend Micro Cloud One is a great fit.
What is AWS Security Hub and How Does It Improve Cloud Security?
AWS Security Hub gathers security data from AWS-native and third-party tools, enabling organizations to detect, prioritize, and respond to security risks efficiently.
How Does AWS Security Hub Work?
Security Hub acts as a single pane of glass for cloud security, consolidating findings from multiple AWS services and third-party security tools. Instead of manually checking different security dashboards, teams get a unified view of their security posture, making it easier to detect vulnerabilities and misconfigurations.
Key Features of AWS Security Hub
Centralized security visibility
Security Hub collects and normalizes security findings from AWS services, such as:
- AWS Config
- Amazon GuardDuty
- AWS IAM Access Analyzer
- AWS Firewall Manager
It also integrates with third-party security solutions, allowing security teams to view and manage risks from a single dashboard rather than juggling multiple security tools.
Automated compliance checks
Security Hub continuously scans AWS environments against well-established security frameworks, including:
- AWS Foundational Security Best Practices
- CIS AWS Foundations Benchmark
- PCI DSS (Payment Card Industry Data Security Standard)
- NIST 800-53
These automated checks help organizations identify misconfigurations and maintain compliance with industry regulations without manual effort.
Findings aggregation and normalization
One of Security Hub’s key benefits is its ability to aggregate and standardize findings from multiple sources. It converts security data into the AWS Security Finding Format (ASFF), making it easier for teams to correlate, analyze, and act on security issues.
Hassle-free integration with AWS and third-party tools
AWS Security Hub works natively with:
- AWS Lambda for automated security response actions
- Amazon EventBridge to trigger alerts and workflows
- AWS Security Lake for in-depth analytics and threat detection
It also supports integrations with external security platforms, helping organizations maintain a broader and more effective security posture.
Security insights and risk prioritization
Security Hub analyzes trends and identifies high-risk security findings, enabling teams to prioritize and remediate threats before they escalate. By focusing on the most critical issues first, organizations can reduce their attack surface and improve overall security.
Automation and response actions
Security Hub enables automated responses using AWS Lambda. For example, it can:
- Isolate compromised resources
- Revoke risky permissions
- Notify security teams based on predefined playbooks
These automated actions enhance incident response, allowing security teams to act quickly without manual intervention.
Why should you use AWS Security Hub?
AWS Security Hub is essential for organizations looking to:
- Improve cloud security visibility across multiple AWS accounts and services
- Automate compliance checks to meet regulatory requirements
- Standardize security findings for easier analysis and response
- Reduce manual security workload with automated remediation
What Role Does AWS Security Hub Play in CSPM?
As a cloud security posture management (CSPM) tool, AWS Security Hub helps organizations strengthen their cloud security by providing continuous visibility, compliance monitoring, and automated security operations. It plays a crucial role in:
- Identifying security misconfigurations across AWS accounts and services before they become potential threats.
- Ensuring continuous compliance monitoring by aligning configurations with industry security standards and best practices.
- Simplifying incident response through automated security workflows that reduce manual intervention.
- Improving security operations efficiency by consolidating security alerts and minimizing alert fatigue for security teams.
AWS Security Hub serves as a foundational component for maintaining security and compliance in AWS environments.
How Do Organizations Use AWS CSPM?
AWS CSPM helps businesses strengthen cloud security by automating misconfiguration detection, ensuring compliance, simplifying threat response, and simplifying security operations.
Here are a few real-world use cases demonstrating its impact.
Preventing Data Breaches with Automated Misconfiguration Detection
Scenario
A financial services company stores sensitive customer data in Amazon S3 but struggles to secure its environment due to rapid cloud expansion.
AWS CSPM Solution
- AWS Security Hub continuously scans S3 configurations, flagging publicly accessible buckets and unencrypted data storage.
- Automated remediation via AWS Lambda corrects misconfigurations in real time.
- Security teams receive alerts through integrations with ticketing systems like ServiceNow, ensuring quick action.
Outcome
The company prevents accidental data leaks, meets compliance standards, and reduces security misconfiguration risks.
Achieving Continuous Compliance in a Regulated Industry
Scenario
A healthcare provider using AWS must comply with HIPAA and ensure all patient data is securely stored and transmitted.
AWS CSPM Solution
- AWS Config continuously monitors cloud resources to enforce encryption, logging, and least-privilege access policies.
- AWS Security Hub runs compliance checks against CIS AWS Foundations Benchmark and AWS Foundational Security Best Practices.
- Findings are integrated into Jira for tracking, enabling DevOps and security teams to collaborate on necessary fixes.
Outcome
The healthcare provider maintains an auditable security posture, reduces compliance risks, and ensures patient data remains protected.
Simplifying Security Operations with Automated Threat Response
Scenario
A global e-commerce company experiences frequent brute-force login attempts and unauthorized API access.
AWS CSPM Solution
- Amazon GuardDuty detects suspicious authentication attempts.
- Security Hub aggregates these findings and triggers an AWS Lambda function that blocks the attacker’s IP via AWS WAF.
- Security teams are notified through PagerDuty for further investigation.
Outcome
The company stops potential account takeovers in real-time, minimizing the risk of fraud and customer data breaches.
Reducing Cloud Security Complexity for a Fast-Growing Startup
Scenario
A SaaS startup expanding rapidly struggles with cloud security visibility across multiple AWS accounts.
AWS CSPM Solution
- AWS Security Hub consolidates security findings from all AWS accounts into a single dashboard.
- Amazon Detective provides deeper investigation capabilities, helping the team understand attack patterns.
- Automated security workflows in AWS Systems Manager remediate common security gaps.
Outcome
The startup gains full visibility into its security posture, reduces manual security efforts, and ensures a scalable, secure cloud environment.
AWS CSPM Best Practices
Implementing AWS CSPM effectively requires the following best practices tailored to cloud security:
1. Enforce Least Privilege Access
- Use IAM policies to grant only necessary permissions to users and applications.
- Regularly audit IAM roles and permissions to eliminate excessive access rights.
2. Enable AWS Security Hub & GuardDuty
- AWS Security Hub aggregates security alerts and compliance findings across AWS services.
- GuardDuty provides threat intelligence by detecting malicious activity within AWS environments.
3. Monitor S3 Bucket Configurations
- Ensure that S3 buckets are private by default and use encryption.
- Enable logging and access controls to track unauthorized access attempts.
4. Automate Security Audits
- Use AWS Config to track configuration changes and enforce security rules.
- Implement AWS Lambda functions to automatically remediate non-compliant configurations.
5. Integrate with SIEM & SOAR Solutions
- Centralize security logs using AWS CloudTrail and Amazon CloudWatch.
- Integrate with SIEM platforms like Splunk or AWS-native solutions for real-time threat analysis.
The Bottom Line
AWS CSPM helps organizations of all sizes protect their cloud infrastructure by identifying misconfigurations, enforcing compliance, automating responses, and simplifying security operations.
If you're looking to enhance AWS CSPM within your environment, consider implementing a comprehensive security framework that includes visibility, continuous monitoring, compliance, and automated remediation.



